RBAC
The Role Based Access Control (RBAC) feature in ADOC allows you to implement authorization control across the entire ADOC application. With RBAC, each feature of ADOC can be accessed by users only if they have the required permissions.
The various components of RBAC are as follows.
- Applications: ADOC has two applications. Admin Central and Data Observability. The Admin Central application consists of all the configurations which are part of the User Management and Access icon. The Data Observability application consists of all other ADOC features other than the admin settings.
- Roles: The Admin Central application has two roles; Admin and User. The Data Observability application has three roles; Viewer, Editor, and Owner. The list of actions that you can perform with each of these roles is explained in further section of this document.
- Features: Both the Admin Central and Data Observability applications have some features. The role assigned to a user determines the features that can be accessed by the user.
You can view the roles assigned to a user, for both the applications, by navigating to the user detail view.
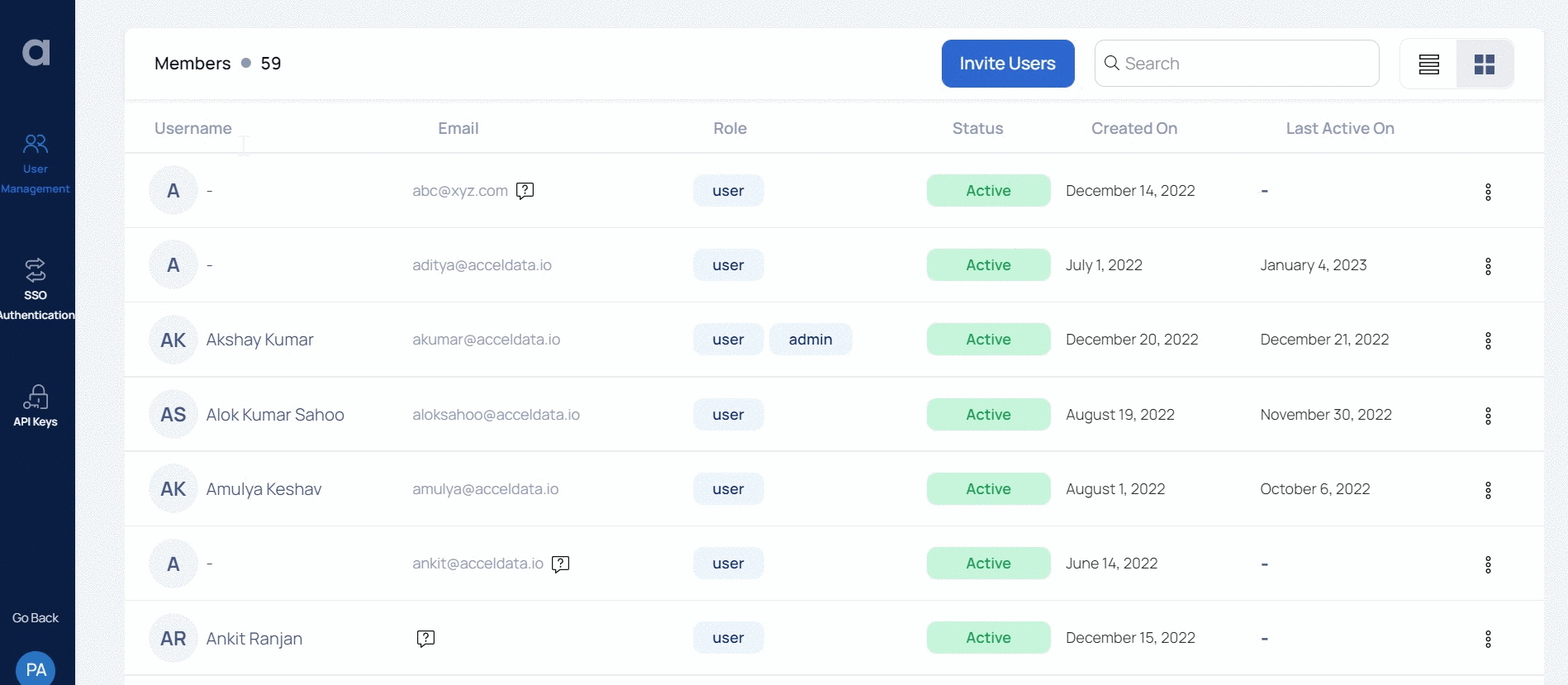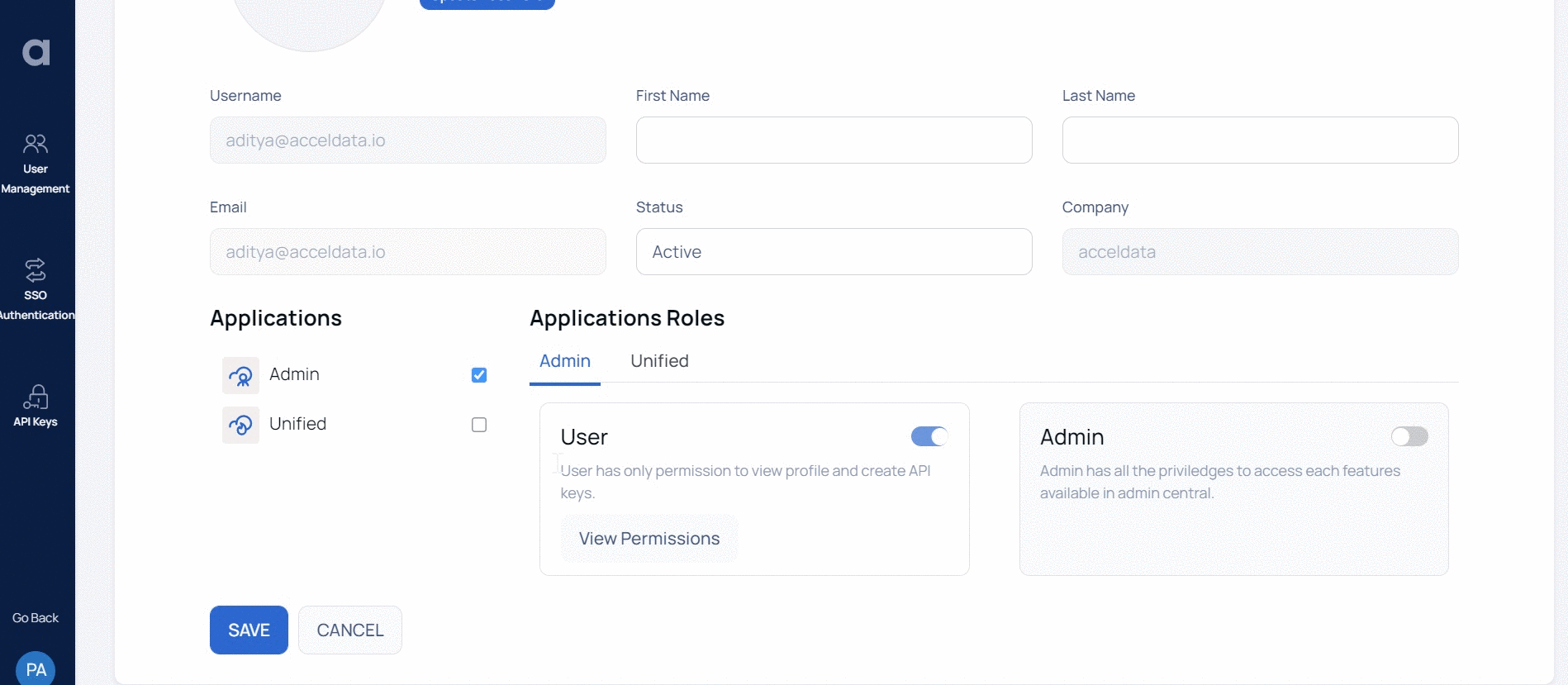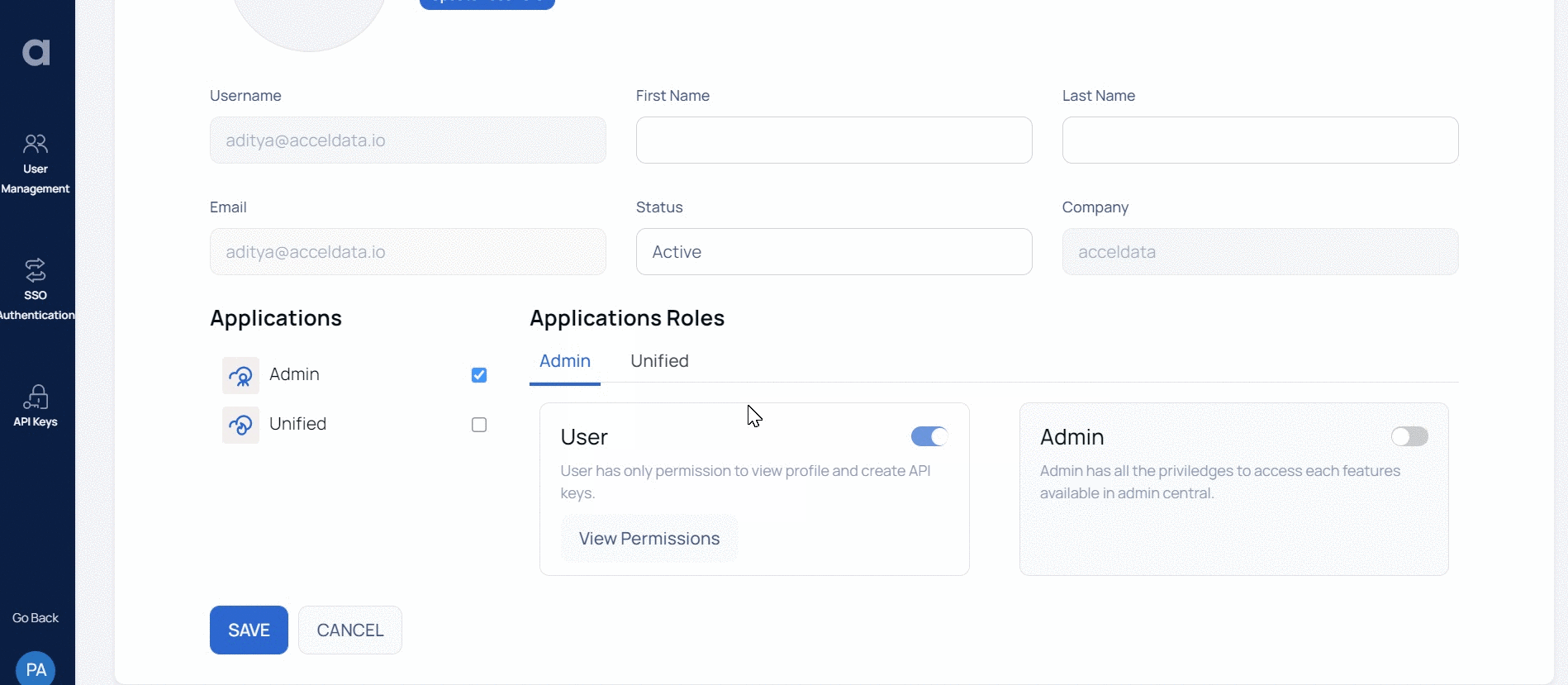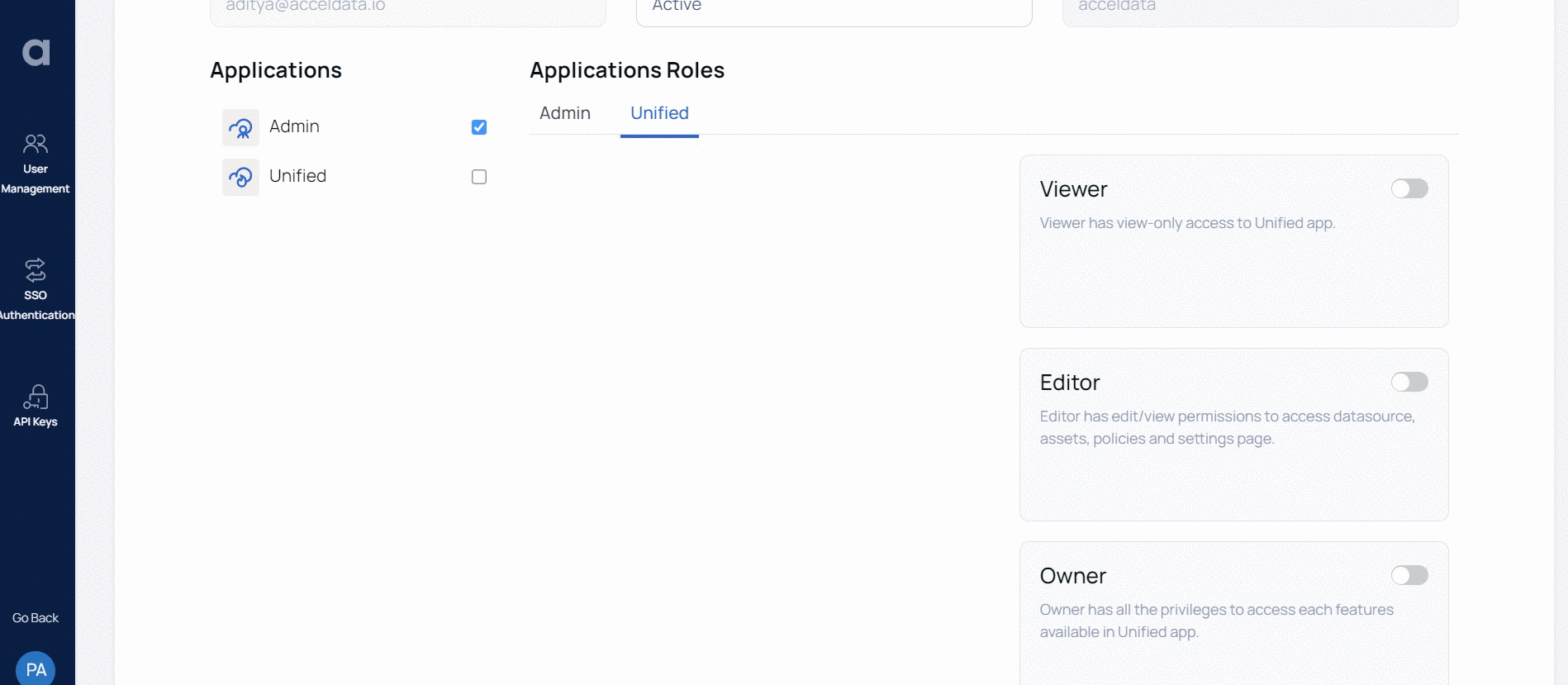
The various tasks that you can perform with each feature in Admin Central application is described in the following table.
| Feature | User Role | Admin Role |
|---|---|---|
| API Keys | Create, Modify, View | Create, Modify, View |
| SSO Settings | Cannot view | Create, Modify, View |
| User Profile | Modify, View | Create, Modify, View |
| Users | Cannot view | Create, Modify, View |
Administration
| Feature Group | Feature Name | Description | Create | Modify | View |
|---|---|---|---|---|---|
| API Keys | API Keys | API keys are handled by users to ensure secure data access. | |||
| Account Configuration | SSO Settings | Single Sign-On configuration for user login | |||
| User Management | User Roles | Limits user operations by assigning permissions. | |||
| User Groups | Create and manage the user groups | ||||
| Users | Create and manage users |
User Profile :View and manage your personal profile and API keys. All ADOC users are granted implicit permission.
The various tasks that you can perform with each feature in Data Observability application is described in the following table.
| Feature | Owner | Editor | Viewer |
|---|---|---|---|
| Manage Budget | Create, Modify, View | Cannot view | Cannot view |
| Organization Chargeback | Create, Modify, View | Cannot view | Cannot view |
| Cost Centre | Create, Modify, View | Cannot view | Cannot view |
| Organization Unit | Create, Modify, View | Cannot view | Cannot view |
| Compute Monitor | Create, Modify, View | Create, Modify, View | View |
| Asset | View | View | View |
| Asset Customer Metadata | Create, Modify, View | Cannot view | View |
| Manage Asset Lineage | Create, Modify, View | Cannot view | View |
| Manage Asset Settings | Modify, View | Modify, View | View |
| Business Assets | Create, Modify, View | Cannot view | View |
| Data Policy Templates | Create, Modify, View | Cannot view | View |
| Data Tags | Create, Modify, View | Cannot view | View |
| Business Glossary | Create, Modify, View | Cannot view | View |
| Execution Jobs | Modify, View | Modify, View | View |
| Policies | Create, Modify, View | Cannot view | Cannot view |
| Query Analyzer | Create | Create | Cannot view |
| Reliability Dashboard | View | View | View |
| Import/Export Policy | Create | Create | Cannot view |
| Visual View | Create, Modify, View | Cannot view | View |
| Manage Datasources | Create, Modify, View | View | View |
| Manage Tags | Create, Modify, View | Cannot view | View |
| Data Plane | Create, Modify, View | View | View |
| Manage Alerts | Create, Modify, View | Cannot view | View |
| Pipeline Events | Create, Modify, View | Cannot view | View |
| Manage Pipelines | Create, Modify, View | Cannot view | View |
| Data Persistence | Modify, View | Cannot view | Cannot view |
| Data Protection | Modify, View | Cannot view | Cannot view |
| Notifications | Create, Modify, View | Cannot view | View |
Compute
| Feature Group | Feature Name | Description | Owner | Editor | Viewer |
|---|---|---|---|---|---|
| Chargeback | Manage Budget | Create and manage budget for the organization. | |||
| Organization Chargeback | Chargeback for the organizational units. | ||||
| Cost Centers | Create and manage cost centers for the organization. |
- The RBAC roles and permissions are also applicable for API operations.
- If a user is assigned multiple roles, the user gets a union of permissions from all the assigned roles. If a user is assigned two roles which have a different permission set (example owner and viewer), the role with supreme permissions (in this case owner) takes the precedence.