Title
Create new category
Edit page index title
Edit category
Edit link
ODP Password Obfuscation Guide
This document provides step-by-step instructions for implementing password obfuscation in ODP stack components.
Using OBF Password Obfuscation
OBF password obfuscation converts plaintext passwords into an obfuscated format to prevent casual exposure in configuration files. This method is supported for components that explicitly state OBF format compatibility.
Locate Jetty Utilities
Run the following commands to locate the required Jetty utility JAR file:
cd /usr/odp/3.3.6.3-1find hadoop* -iname jetty-util-*.jarExample output:
hadoop/lib/jetty-util-9.4.51.v20230217.jar hadoop/lib/jetty-util-ajax-9.4.51.v20230217.jar hadoop/client/jetty-util-9.4.51.v20230217.jar hadoop/client/jetty-util-ajax-9.4.51.v20230217.jar hadoop/client/jetty-util-ajax.jar hadoop-hdfs/lib/jetty-util-9.4.51.v20230217.jarGenerate an OBF Password
Use the Jetty Password utility to generate an obfuscated password:
java -cp hadoop/lib/jetty-util-9.4.51.v20230217.jar \ org.eclipse.jetty.util.security.Password \ <keystore-or-truststore-password>Example:
java -cp hadoop/lib/jetty-util-9.4.51.v20230217.jar \ org.eclipse.jetty.util.security.Password \ Hadoop@123Example output:
Hadoop@123 OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq MD5:d61eb912413c69c46d34b847ef660caaUpdate configuration files
- Add the generated OBF value to the ssl.*.password properties.
- Replace all plaintext passwords with the OBF string OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq in the required configuration files.
- Apply these steps to all components that explicitly support the OBF format.
Securing passwords in Ambari
In ODP-Ambari, database passwords and SSL truststore passwords stored in ambari.properties can be secured using the Ambari Server utility and OBF password obfuscation.
root@ub22-33611-1:~# ambari-server setup-securityUsing python /usr/bin/python3.11Security setup options...===========================================================================Choose one of the following options: [1] Enable HTTPS for Ambari server. [2] Encrypt passwords stored in ambari.properties file. [3] Setup Ambari kerberos JAAS configuration. [4] Setup truststore. [5] Import certificate to truststore.===========================================================================Enter choice, (1-5): 2Please provide master key for locking the credential store:Re-enter master key:Do you want to persist master key. If you choose not to persist, you need to provide the Master Key while starting the ambari server as an env variable named AMBARI_SECURITY_MASTER_KEY or the start will prompt for the master key. Persist [y/n] (y)? yAdjusting ambari-server permissions and ownership...Ambari Server 'setup-security' completed successfully.Verify that passwords are referenced by alias in ambari.properties:
root@ub22-3362-1:/etc/ambari-server/conf# grep -ir -e "password" -e "secret" -e "Hadoop@123"ambari.properties:security.passwords.encryption.enabled=trueambari.properties:server.jdbc.rca.user.passwd=${alias=ambari.db.password}ambari.properties:server.jdbc.user.passwd=${alias=ambari.db.password}ambari.properties:ssl.trustStore.password=${alias=ambari.ssl.trustStore.password}root@ub22-33611-1:/etc/ambari-server/conf#Obfuscate SSL Password in https.pass.txt
The SSL password stored in /var/lib/ambari-server/keys/https.pass.txt can be updated in OBF format using Jetty utilities:
root@ub22-33611-1:~# java -cp /usr/lib/ambari-server/jetty-util-9.4.43.v20210629.jar \> org.eclipse.jetty.util.security.Password \> <<PASSWORD>>2025-05-27 15:54:19.535:INFO::main: Logging initialized @94ms to org.eclipse.jetty.util.log.StdErrLog[PASSWORD]OBF:<< hash generated >>MD5:<< md5 hash >>Confirm that the password is updated:
root@ub22-33611-1:~# cat /var/lib/ambari-server/keys/https.pass.txtOBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqZooKeeper
OBF password obfuscation is supported for SSL-related properties.
Generate an OBF Password
Use Jetty utilities to generate an obfuscated password:
java -cp lib/jetty-util-9.4.53.v20231009.jar org.eclipse.jetty.util.security.Password <SSL_Password>Example:
java -cp zookeeper/lib/jetty-util-9.4.53.v20231009.jar org.eclipse.jetty.util.security.Password Hadoop@123Expected output:
[root@rl9-zk-ssl 3.3.6.3-1]# java -cp zookeeper/lib/jetty-util-9.4.53.v20231009.jar org.eclipse.jetty.util.security.Password Hadoop@1232025-06-11 18:33:12.737:INFO::main: Logging initialized @87ms to org.eclipse.jetty.util.log.StdErrLogHadoop@123OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqMD5:d61eb912413c69c46d34b847ef660caaUse the OBF value (for example, OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq) in configuration.
Configure OBF Passwords in Ambari UI
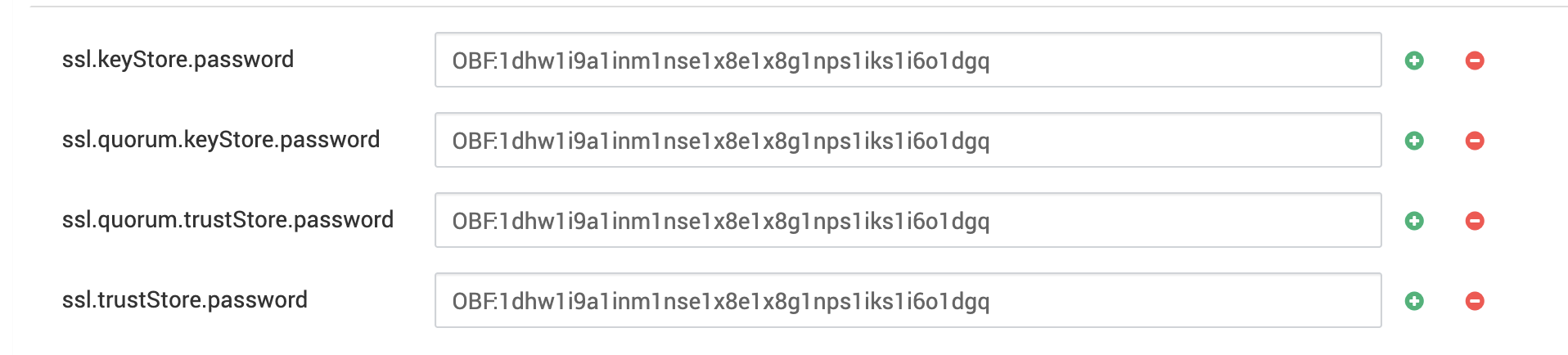
Update the following ZooKeeper SSL properties in Ambari UI:
ssl.keyStore.password=<OBF:<obfuscate-password>>ssl.quorum.keyStore.password=<OBF:<obfuscate-password>>ssl.quorum.trustStore.password=<OBF:<obfuscate-password>>An example is shown below in the screenshot.
Verify Configuration
After restarting ZooKeeper, verify that the updated properties are applied:
[root@rl9-zk-ssl 3.3.6.3-1]# grep -irn password /etc/zookeeper/conf/*/etc/zookeeper/conf/zoo.cfg:39:ssl.keyStore.password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq/etc/zookeeper/conf/zoo.cfg:42:ssl.quorum.keyStore.password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq/etc/zookeeper/conf/zoo.cfg:44:ssl.quorum.trustStore.password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq/etc/zookeeper/conf/zoo.cfg:46:ssl.trustStore.password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqHadoop
1. Ambari UI Verification
In the ODP-Ambari UI, no Hadoop service passwords (HDFS, YARN, MR) appear to be exposed.
2. Verify Passwords from the Hadoop Configuration Directory
Passwords can be reviewed in the saved XML configuration files located at:
/etc/hadoop/3.3.6.3-1/0/Run the following command:
grep -irn "password" * -A 2Results
secure/ssl-client.xml:24: <name>ssl.client.truststore.password</name>secure/ssl-client.xml-25- <value>Hadoop@123</value>secure/ssl-client.xml-26- </property>--ssl-client.xml:9: <name>ssl.client.keystore.password</name>ssl-client.xml-10- <value>Hadoop@123</value>ssl-client.xml-11- </property>--ssl-client.xml:24: <name>ssl.client.truststore.password</name>ssl-client.xml-25- <value>Hadoop@123</value>ssl-client.xml-26- </property>ssl-server.xml:4: <name>ssl.server.keystore.keypassword</name>ssl-server.xml-5- <value>Hadoop@123</value>ssl-server.xml-6- </property>--ssl-server.xml:14: <name>ssl.server.keystore.password</name>ssl-server.xml-15- <value>Hadoop@123</value>ssl-server.xml-16- </property>--ssl-server.xml:29: <name>ssl.server.truststore.password</name>ssl-server.xml-30- <value>Hadoop@123</value>ssl-server.xml-31- </property>3. Create JCEKS for SSL Client Passwords
Run the following commands on every cluster node:
Create ssl.client.keystore.password
hadoop credential create ssl.client.keystore.password \ -value Hadoop@123 \ -provider jceks://file/etc/hadoop/conf/ssl-client.jceksResponse:
WARNING: You have accepted the use of the default provider passwordby not configuring a password in one of the two following locations: * In the environment variable HADOOP_CREDSTORE_PASSWORD * In a file referred to by the configuration entry hadoop.security.credstore.java-keystore-provider.password-file.Please review the documentation regarding provider passwords inthe keystore passwords section of the Credential Provider APIContinuing with the default provider password.ssl.client.keystore.password has been successfully created.Provider jceks://file/etc/hadoop/conf/ssl-client.jceks was updated.Create ssl.client.truststore.password
hadoop credential create ssl.client.truststore.password \ -value Hadoop@123 \ -provider jceks://file/etc/hadoop/conf/ssl-client.jceksResponse:
WARNING: You have accepted the use of the default provider passwordby not configuring a password in one of the two following locations: * In the environment variable HADOOP_CREDSTORE_PASSWORD * In a file referred to by the configuration entry hadoop.security.credstore.java-keystore-provider.password-file.Please review the documentation regarding provider passwords inthe keystore passwords section of the Credential Provider APIContinuing with the default provider password.ssl.client.truststore.password has been successfully created.Provider jceks://file/etc/hadoop/conf/ssl-client.jceks was updated.Then update the provider path in Ambari UI.
4. Create JCEKS for SSL Server Passwords
Repeat the same procedure for SSL server keys.
Keystore Key Password
hadoop credential create ssl.server.keystore.keypassword \ -provider jceks://file/etc/hadoop/conf/ssl-server.jceks \ -value Hadoop@123Response:
WARNING: You have accepted the use of the default provider passwordby not configuring a password in one of the two following locations: * In the environment variable HADOOP_CREDSTORE_PASSWORD * In a file referred to by the configuration entry hadoop.security.credstore.java-keystore-provider.password-file.Please review the documentation regarding provider passwords inthe keystore passwords section of the Credential Provider APIContinuing with the default provider password.ssl.server.keystore.keypassword has been successfully created.Provider jceks://file/etc/hadoop/conf/ssl-server.jceks was updated.Truststore Password
hadoop credential create ssl.server.truststore.password \ -provider jceks://file/etc/hadoop/conf/ssl-server.jceks \ -value Hadoop@123Keystore Password
hadoop credential create ssl.server.keystore.password \ -provider jceks://file/etc/hadoop/conf/ssl-server.jceks \ -value Hadoop@123Verify the Server Keys
hadoop credential list -provider jceks://file/etc/hadoop/conf/ssl-server.jceksResponse:
ssl.server.truststore.passwordssl.server.keystore.passwordssl.server.keystore.keypasswordVerify Client Keys
hadoop credential list -provider jceks://file/etc/hadoop/conf/ssl-client.jceksResponse:
ssl.client.keystore.passwordssl.client.truststore.password5. Add Credential Provider Path in Ambari UI
Navigate to HDFS → Configs → custom ssl-client and add:
hadoop.security.credential.provider.path=jceks://file/etc/hadoop/conf/ssl-client.jceksNavigate to HDFS → Configs → custom ssl-server and add:
hadoop.security.credential.provider.path=jceks://file/etc/hadoop/conf/ssl-server.jceks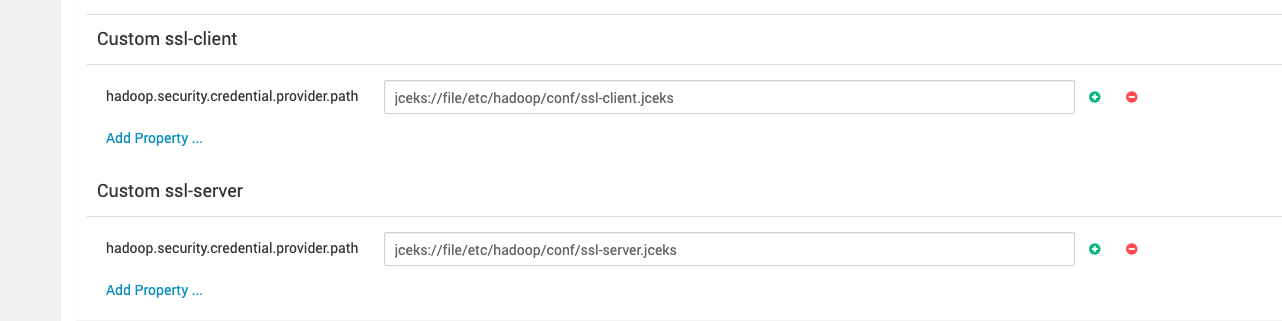
Client Configurations
ssl.client.keystore.password=${alias:ssl.client.keystore.password}ssl.client.truststore.password=${alias:ssl.client.truststore.password}Server Configurations
ssl.server.keystore.keypassword=${ssl.server.keystore.keypassword}ssl.server.keystore.password=${alias:ssl.server.keystore.password}ssl.server.truststore.password=${alias:ssl.server.truststore.password}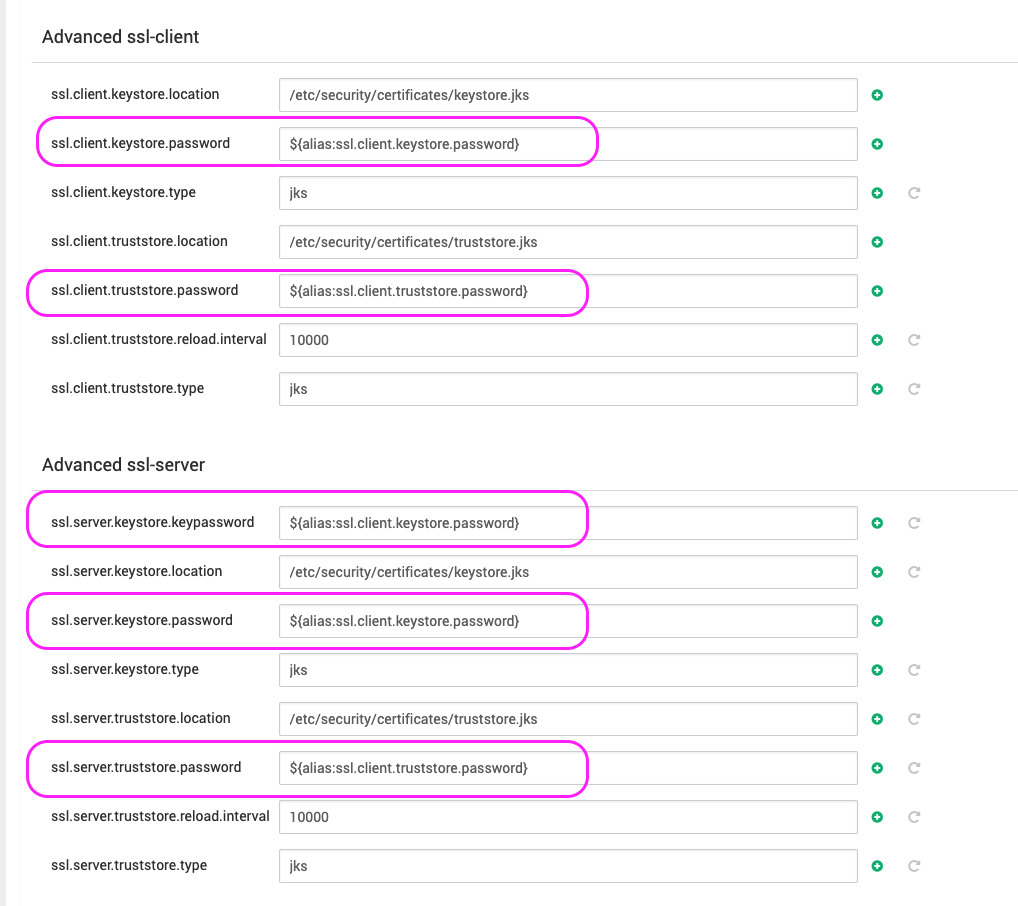
6. File Permissions
Run:
chown hdfs:hadoop ssl-client.jceks .ssl-client.jceks.crc ssl-server.jceks .ssl-server.jceks.crcchmod 640 ssl-client.jceks .ssl-client.jceks.crc ssl-server.jceks .ssl-server.jceks.crcCheck files:
ls -la /etc/hadoop/conf/ | grep jceksResponse:
[root@odpnode1-336 conf]# ls -la /etc/hadoop/conf/ | grep jceks-rw-r----- 1 hdfs hadoop 1000 Dec 1 12:00 ssl-client.jceks-rw-r----- 1 hdfs hadoop 16 Dec 1 12:00 .ssl-client.jceks.crc-rw-r----- 1 hdfs hadoop 1486 Dec 1 12:03 ssl-server.jceks-rw-r----- 1 hdfs hadoop 20 Dec 1 12:03 .ssl-server.jceks.crc7. Restart HDFS
Restart the HDFS service.
All services started successfully and sample jobs executed without issues.
8. Cross Verification After Changes
cd /etc/hadoop/confgrep -irn "password" ssl-*.xml -A 2Response:
ssl-client.xml:14: <name>ssl.client.keystore.password</name>ssl-client.xml:15: <value>${alias:ssl.client.keystore.password}</value>ssl-client.xml-16- </property>ssl-client.xml-17---ssl-client.xml:29: <name>ssl.client.truststore.password</name>ssl-client.xml:30: <value>${alias:ssl.client.truststore.password}</value>ssl-client.xml-31- </property>ssl-client.xml-32---ssl-server.xml:9: <name>ssl.server.keystore.keypassword</name>ssl-server.xml:10: <value>${ssl.server.keystore.keypassword}</value>ssl-server.xml-11- </property>ssl-server.xml-12---ssl-server.xml:19: <name>ssl.server.keystore.password</name>ssl-server.xml:20: <value>${alias:ssl.server.keystore.password}</value>ssl-server.xml-21- </property>ssl-server.xml-22---ssl-server.xml:34: <name>ssl.server.truststore.password</name>ssl-server.xml:35: <value>${alias:ssl.server.truststore.password}</value>ssl-server.xml-36- </property>ssl-server.xml-37-####
Tez
No passwords are exposed in the configuration. Password obfuscation is not applicable.
HBase
HBase initially reads configuration from the XML files. However, later this key–value requirement gets overridden by the Hadoop configuration present in the classpath under hbase-env.sh, where ssl-server.xml and then ssl-client.xml are loaded in order. As a result, HBase ends up using the credential provider path from the Hadoop configuration to fetch credentials instead of the values provided in hbase-site.xml.
To resolve this, we need to add the required entry while creating Hadoop credentials on each node for the ssl-client.jceks step.
hadoop credential create ssl.server.keystore.password -value Hadoop@123 -provider jceks://file/etc/hadoop/conf/ssl-client.jcekshadoop credential create ssl.server.keystore.keypassword -value Hadoop@123 -provider jceks://file/etc/hadoop/conf/ssl-client.jcekshadoop credential create ssl.server.truststore.password -value Hadoop@123 -provider jceks://file/etc/hadoop/conf/ssl-client.jceksOBF format password obfuscation is supported and can be enabled.
Add the OBF passwords to hbase-site.xml:
ssl.server.keystore.keypassword=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqssl.server.keystore.password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqFlink
Flink supports password obfuscation in OBF format. You can configure it either from the Ambari UI or directly in the backend configuration files.
Configure from Ambari UI
- Go to Flink > Configs > Advanced flink-conf.
- Add the OBF passwords:
security.ssl.internal.key-password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqsecurity.ssl.internal.keystore-password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqsecurity.ssl.internal.truststore-password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqsecurity.ssl.rest.key-password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqsecurity.ssl.rest.keystore-password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqsecurity.ssl.rest.truststore-password=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq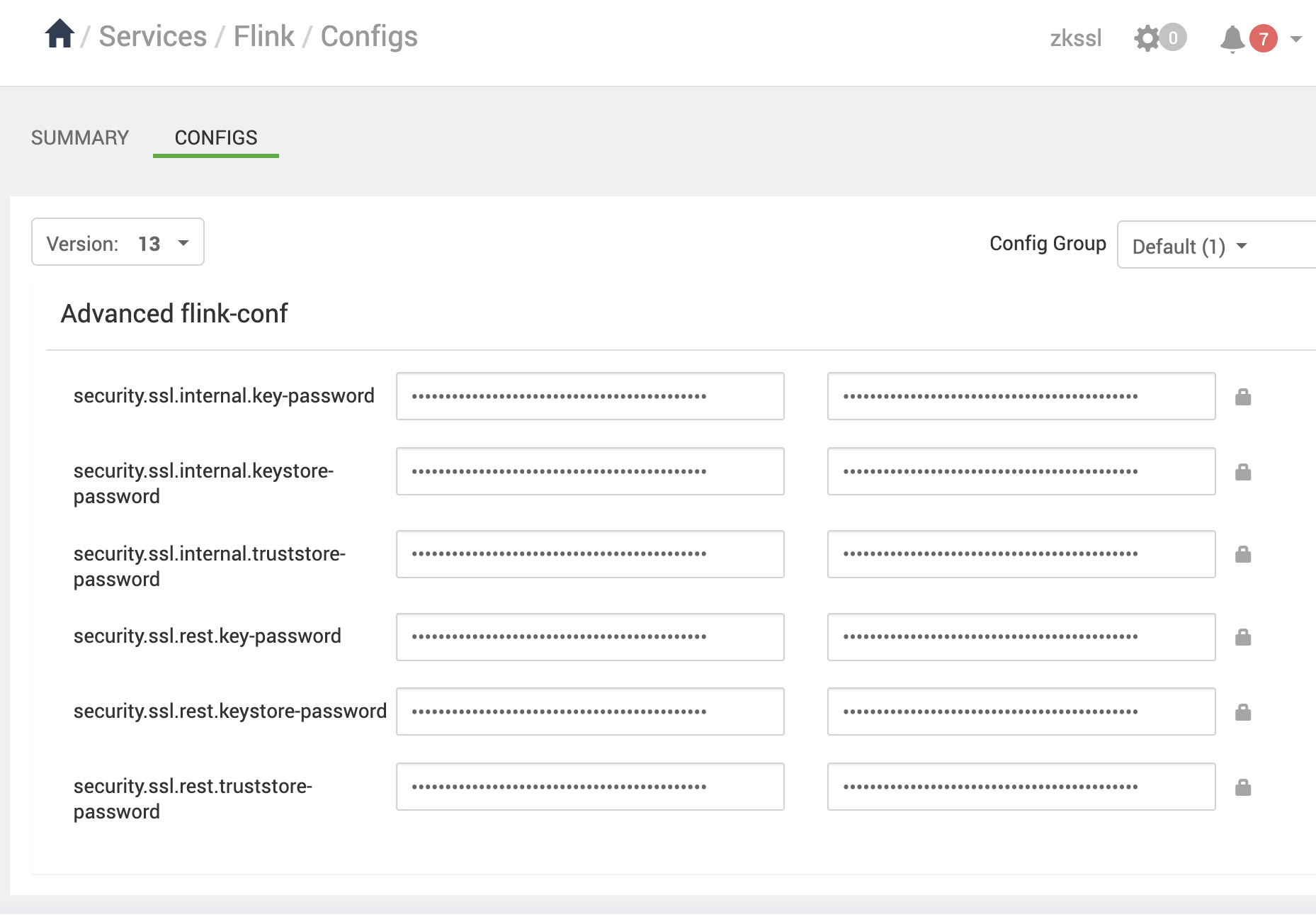
- Restart the Flink service.
Verify in Backend Configuration Files
In /etc/flink/conf/config.yaml
security: ssl: internal: enabled: 'true' key-password: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq truststore-password: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq keystore-password: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq truststore: /etc/security/certificates/truststore.jks keystore: /etc/security/certificates/keystore.jksIn /etc/flink/conf/history-server.conf/config.yaml
security: ssl: rest: keystore-password: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq authentication-enabled: 'false' truststore-password: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq key-password: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq truststore: /etc/security/certificates/truststore.jks keystore: /etc/security/certificates/keystore.jks enabled: 'true' internal: enabled: 'true' key-password: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq truststore-password: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq keystore-password: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq truststore: /etc/security/certificates/truststore.jks keystore: /etc/security/certificates/keystore.jkshistoryserver: archive: fs: dir: hdfs://rl9-zk-ssl.acceldata.ce:8020/apps/odp/flink/completed-jobs/ refresh-interval: '10000' web: address: 0.0.0.0 port: '9022' ssl: enabled: 'true'Post-Configuration Validation
- Flink and History Server should start without errors.
- HS WebUI should be accessible over HTTPS.
- Backend config files will display passwords in OBF format, confirming obfuscation.
Knox
No passwords are exposed.
NiFi and NiFi Registry
Passwords are stored in encrypted format rather than plain text.
Example: nifi.properties
./nifi.properties:115:nifi.security.keyPasswd=8703Ep5pNuqS/pAr||hnGE1NFC/KO7xSabjLaObuyCP2MNuA1BMSQ=./nifi.properties:116:nifi.security.keyPasswd.protected=aes/gcm/256./nifi.properties-117-nifi.security.keystore=/etc/security/certificates/keystore.jks./nifi.properties:118:nifi.security.keystorePasswd=QGZicHq+FfnaG/OR||ALZq7GaoemuV1GIypLRSbG/BQI7SLJPh238=./nifi.properties:119:nifi.security.keystorePasswd.protected=aes/gcm/256./nifi.properties-120-nifi.security.keystoreType=jksKey Points
- Protected attributes (.protected) indicate that the corresponding password value is encrypted.
- No plaintext credentials are stored in configuration files.
Schema Registry
- Database master password is stored in an environment variable.
- SSL key and truststore passwords are stored in OBF format in configuration files.
Generate an OBF Password
Run the following command:
[root@test15 certificates]# java -cp /usr/odp/3.3.6.3-1/hadoop/lib/jetty-util-9.4.57.v20241219.jar org.eclipse.jetty.util.security.Password <<PASSWORD>>2025-05-27 15:54:19.535:INFO::main: Logging initialized @94ms to org.eclipse.jetty.util.log.StdErrLog<<PASSWORD>>OBF:<< hash generated >>MD5:<< md5 hash >>Output includes:
- Plaintext password (for confirmation)
OBF:<<hash generated>>— obfuscated passwordMD5:<<md5 hash>>— hash representation
Example: registry.yaml
[root@rl9-nifi01 registry]# grep -irn password /etc/registry/conf/registry.yaml61: dataSource.password: ${REGISTRY_DB_PASSWORD}92: keyStorePassword: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq95: trustStorePassword: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq104: keyStorePassword: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq107: trustStorePassword: OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq[root@rl9-nifi01 registry]#Sqoop
- Not applicable (NA) — no password obfuscation mechanism required.
HttpFS
No passwords are exposed.
Infra Solr
- Supports password obfuscation using OBF format.
- Passwords are also stored locally as hashed values after configuration.
Generate an OBF Password
Run the following command:
# java -cp /usr/lib/ambari-infra-solr/dist/solrj-lib/jetty-util-9.4.53.v20231009.jar \> org.eclipse.jetty.util.security.Password \> <<PASSWORD>>2025-05-27 15:54:19.535:INFO::main: Logging initialized @94ms to org.eclipse.jetty.util.log.StdErrLog<<PASSWORD>>OBF:<< hash generated >>MD5:<< md5 hash >>*Output includes: *
- Plaintext password (for confirmation)
- OBF:<<hash generated>> — obfuscated password
- MD5:<<md5 hash>> — hash representation
Update Infra Solr Configuration
Use the generated OBF password for both trust store and key store passwords.
Example (/etc/ambari-infra-solr/conf/infra-solr-env.sh):
root@ub22-3362-1:~/acceldata# cat /etc/ambari-infra-solr/conf/infra-solr-env.sh | grep -i passwordSOLR_SSL_KEY_STORE_PASSWORD=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqSOLR_SSL_TRUST_STORE_PASSWORD=OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq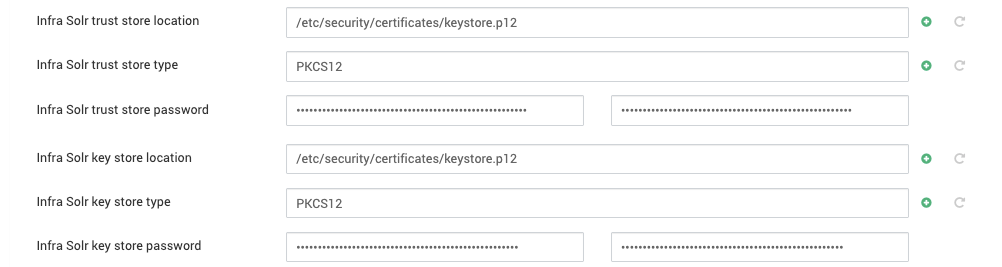
Final Steps
- Save the updated configuration.
- Restart the Infra Solr service.
- Verify that passwords are stored locally in hashed format.
Isilon
No passwords are exposed.
Zeppelin
- Supports password obfuscation using OBF format for SSL configuration.
- Interpreter credentials can be securely stored through Zeppelin’s Credential UI.
Generate an OBF Password
Run the following command:
[root@test15 certificates]# java -cp /usr/odp/current/zeppelin-server/lib/jetty-util-9.4.52.v20230823.jar \> org.eclipse.jetty.util.security.Password \> <<PASSWORD>>2025-05-27 15:54:19.535:INFO::main: Logging initialized @94ms to org.eclipse.jetty.util.log.StdErrLog<<PASSWORD>>OBF:<< hash generated >>MD5:<< md5 hash >>Output includes:
- Plaintext password (for confirmation)
OBF:<<hash generated>>— obfuscated passwordMD5:<<md5 hash>>— hash representation
Add Properties in Ambari
Update the following passwords in Ambari with the generated OBF value:
- Key manager password
- Keystore password
- Truststore password
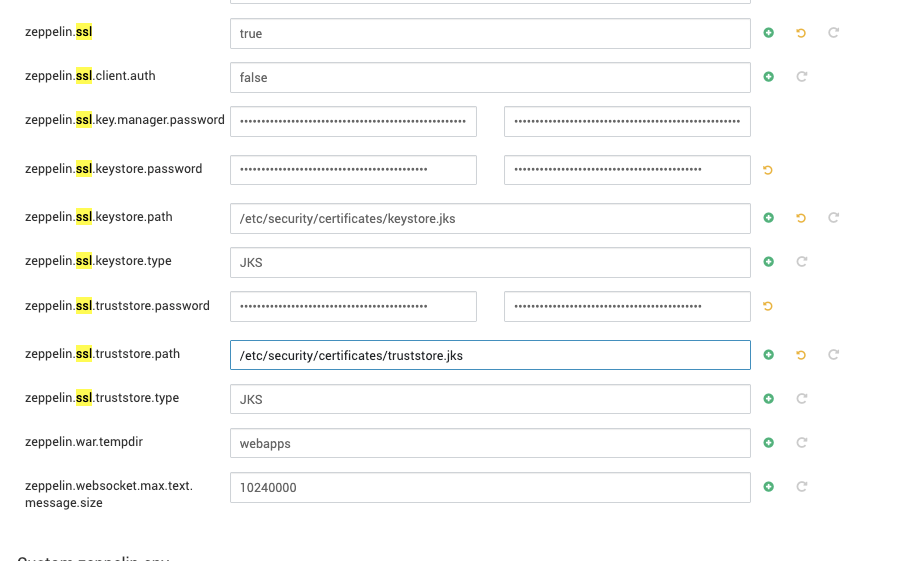
Example (zeppelin-site.xml):
[root@test15 conf]# grep -r -A 1 "password" zeppelin-site.xml <name>zeppelin.ssl.key.manager.password</name> <value>OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq</value>-- <name>zeppelin.ssl.keystore.password</name> <value>OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq</value>-- <name>zeppelin.ssl.truststore.password</name> <value>OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq</value>In Ambari, passwords configured in OBF format show a check mark confirming obfuscation.
Secure Interpreter Credentials
Refer to Apache Zeppelin 0.7.3 Documentation: Data Source Authorization for guidance on securing interpreter passwords.
- Visit
https://<zeppelin host>:9995/#/credential - Add credentials — the Entity field acts similarly to an alias in JCEKS
- Use the stored credentials directly in interpreter settings
Livy
No passwords are exposed.
Spark 3
Use Ambari UI to update Spark related SSL passwords
Generate an OBF Password
Run the following command:
[root@test15 certificates]# java -cp /usr/odp/3.3.6.3-1/hadoop/lib/jetty-util-9.4.57.v20241219.jar org.eclipse.jetty.util.security.Password <<PASSWORD>>2025-05-27 15:54:19.535:INFO::main: Logging initialized @94ms to org.eclipse.jetty.util.log.StdErrLog<<PASSWORD>>OBF:<< hash generated >>MD5:<< md5 hash >>Output includes:
- Plaintext password (for confirmation)
OBF:<<hash generated>>— obfuscated passwordMD5:<<md5 hash>>— hash representation
Example: spark-defaults.conf
[root@vars17-rl8-0 conf]# grep -ir OBFspark.ssl.keyPassword OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqspark.ssl.keyStorePassword OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqspark.ssl.trustStorePassword OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgqAirflow
- No passwords are exposed.
- Password handling is managed by security_credential_helper.py for database connections.
- No SSL passwords are exposed.
JupyterHub
- No passwords are exposed.
- Password handling is managed by security_credential_ helper.py for database connections.
- No SSL passwords are exposed.
Pinot
Sensitive Pinot Controller configuration passwords (including Basic Auth and SSL keystore/truststore passwords) are now encrypted using the Hadoop JCEKS credential store. Passwords are no longer stored in plaintext in configuration files or static environment files. They are securely managed and injected at runtime.
*Key features: *
- Passwords are stored encrypted in a Hadoop JCEKS file.
- A wrapper script extracts the secrets at startup using Ambari’s GenericStorePasswordExtractor.
- Secrets are injected as environment variables and referenced in Pinot configuration through dynamic environment settings.
- No plaintext secrets appear in configuration or static environment files.
Steps
- Create and store passwords in JCEKS: Use the Hadoop credential command to store each password securely in the Hadoop JCEKS credential store.
hadoop credential create pinot.admin.pass \ -value 'your_admin_password' \ -provider jceks://file/etc/security/credential/pinot/pinot.jcekshadoop credential create pinot.keystore.pass \ -value 'your_keystore_password' \ -provider jceks://file/etc/security/credential/pinot/pinot.jcekshadoop credential create pinot.truststore.pass \ -value 'your_truststore_password' \ -provider jceks://file/etc/security/credential/pinot/pinot.jceks- Configure Pinot for dynamic environment variables: In
pinot-controller.conf, reference passwords using environment variable placeholders instead of hardcoding them.
dynamic.env.config=controller.admin.access.control.principals.admin.password,controller.tls.keystore.password,controller.tls.truststore.passwordcontroller.admin.access.control.principals.admin.password=PINOT_ADMIN_PASSWORDcontroller.tls.keystore.password=PINOT_KEYSTORE_PASScontroller.tls.truststore.password=PINOT_TRUSTSTORE_PASS- Wrapper script for secret extraction: Create
/usr/odp/3.3.6.3-1/pinot/start-pinot-controller.shto automatically fetch secrets from the JCEKS store and inject them as environment variables before starting Pinot.
#!/bin/bashexport PINOT_ADMIN_PASSWORD=$( java -cp '.:/etc/hadoop/conf/*:/var/lib/ambari-agent/cred/lib/*' \ org.apache.ambari.security.tools.GenericStorePasswordExtractor \ JCEKS jceks://file/etc/security/credential/pinot/pinot.jceks pinot.admin.pass)export PINOT_KEYSTORE_PASS=$( java -cp '.:/etc/hadoop/conf/*:/var/lib/ambari-agent/cred/lib/*' \ org.apache.ambari.security.tools.GenericStorePasswordExtractor \ JCEKS jceks://file/etc/security/credential/pinot/pinot.jceks pinot.keystore.pass)export PINOT_TRUSTSTORE_PASS=$( java -cp '.:/etc/hadoop/conf/*:/var/lib/ambari-agent/cred/lib/*' \ org.apache.ambari.security.tools.GenericStorePasswordExtractor \ JCEKS jceks://file/etc/security/credential/pinot/pinot.jceks pinot.truststore.pass)exec /usr/odp/3.3.6.3-1/pinot/bin/pinot-admin.sh StartController -config /usr/odp/3.3.6.3-1/pinot/conf/pinot-controller.conf- Update systemd service
ExecStart=/usr/odp/3.3.6.3-1/pinot/start-pinot-controller.shBenefits
- No plaintext passwords in config or environment files.
- Centralized and secure password management using Hadoop JCEKS.
- Easy password rotation without changing Pinot configs.
- Compliant with security best practices for production systems.
References
- Apache Pinot Dynamic Environment Config
- Hadoop Credential Provider API
- Ambari GenericStorePasswordExtractor
In summary: Passwords are encrypted in a JCEKS file, extracted securely at runtime, and injected into Pinot Controller using dynamic environment variables—ensuring no plaintext secrets are ever present on disk or in process listings.
Hue
- No passwords are exposed.
- Password handling is managed by security_credential_ helper.py.
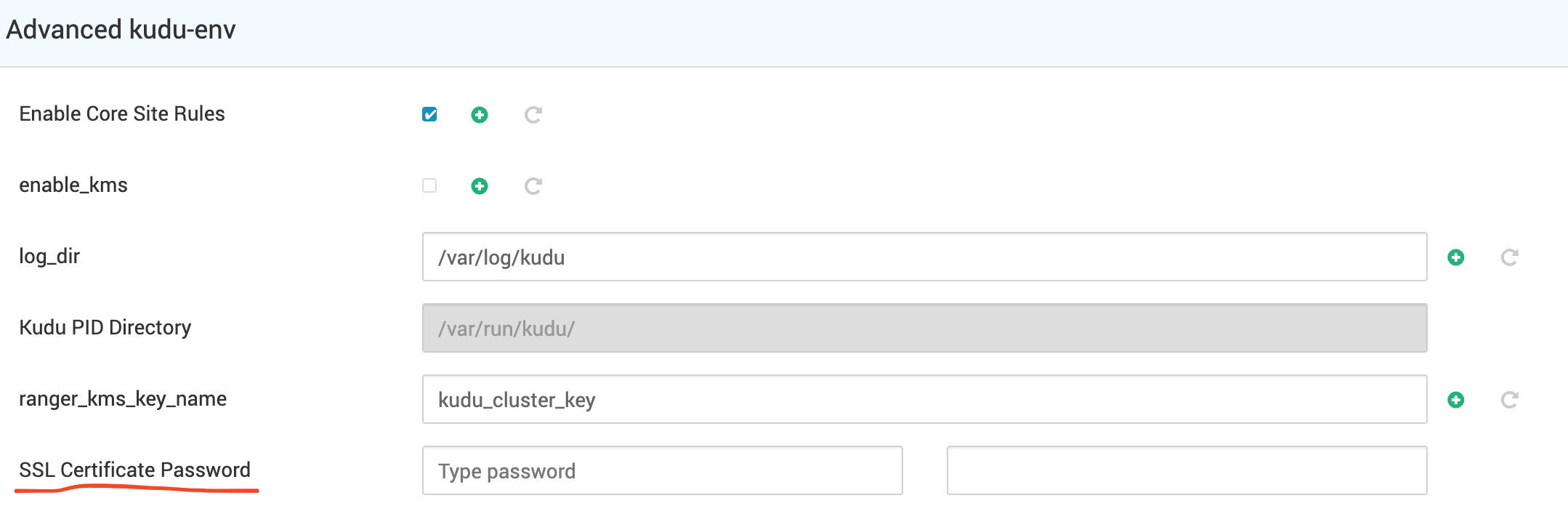
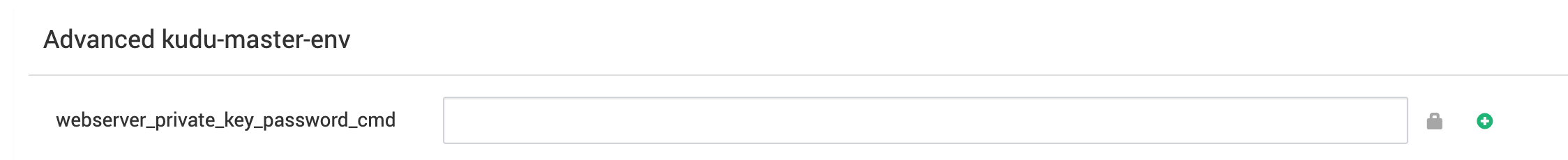
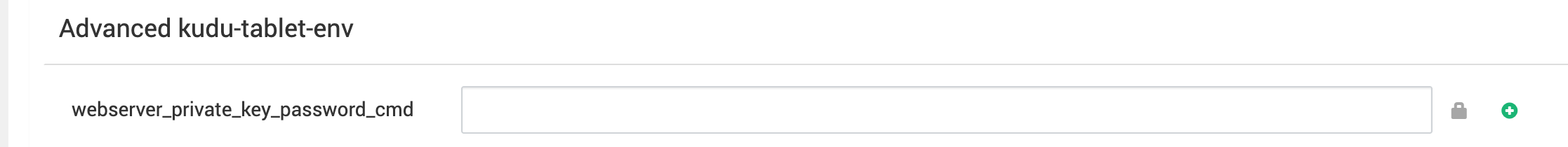
Kudu
- Passwords have never been exposed.
- A new option simplifies SSL support:
- If you set SSL Certificate Password without specifying a custom password retrieval script, Kudu now uses security_credential_helper.py to save and retrieve the password automatically.
- You can still override this behavior by setting specific options in the master and tablet server configurations.
Druid
No passwords are exposed.
Hive
No passwords are exposed.
Ranger
No passwords are exposed.
Cruise Control 2/3
- SSL-related passwords that were previously exposed are now securely managed by Ambari automation using JCEKS.
- No additional user action is required.
Kafka 2/3
- SSL-related passwords that were previously exposed are now securely managed by Ambari automation using JCEKS.
- No additional user action is required.
Kafka 2 Connect
- SSL-related passwords that were previously exposed are now securely managed by Ambari automation using JCEKS.
- No additional user action is required.
Kafka 3 Connect
- SSL-related passwords that were previously exposed are now securely managed by Ambari automation using JCEKS.
- No additional user action is required.
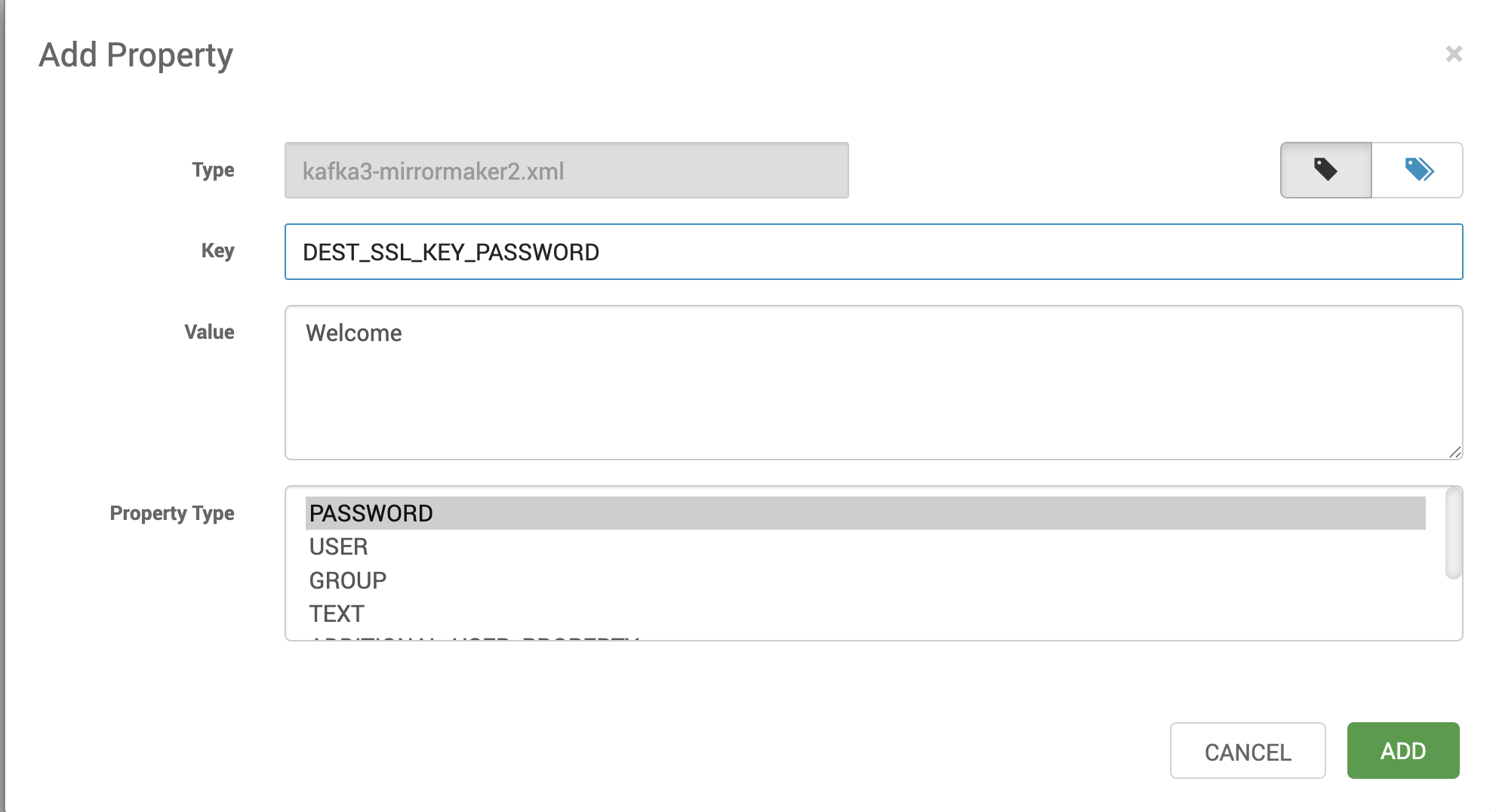
Kafka 2 Mirror Maker
- All configurations must be provided under Advanced kafka-mirrormaker2 in Ambari.
- Any property ending with .password must reference an environment variable rather than storing the value directly.
Example Configuration (Advanced kafka-mirrormaker2)
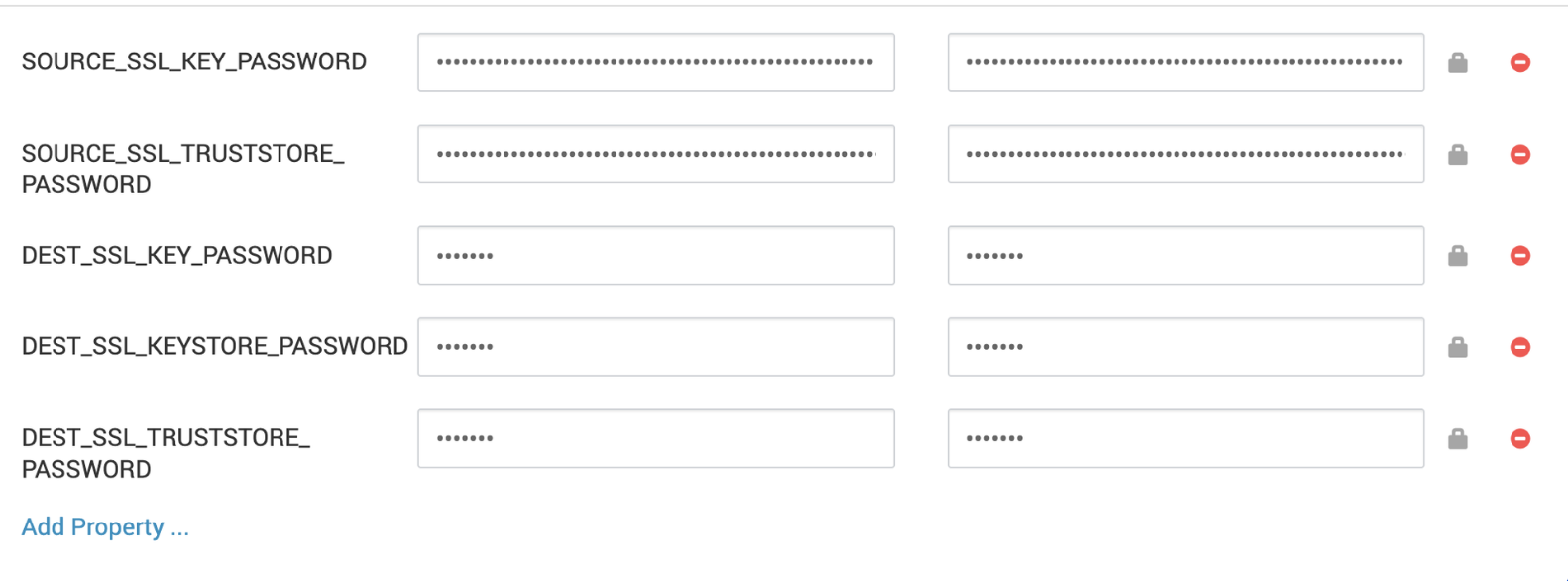
source.ssl.key.password=${env:SOURCE_SSL_KEY_PASSWORD}source.ssl.keystore.password=${env:SOURCE_SSL_KEYSTORE_PASSWORD}source.ssl.truststore.password=${env:SOURCE_SSL_TRUSTSTORE_PASSWORD}dest.ssl.key.password=${env:DEST_SSL_KEY_PASSWORD}dest.ssl.keystore.password=${env:DEST_SSL_KEYSTORE_PASSWORD}dest.ssl.truststore.password=${env:DEST_SSL_TRUSTSTORE_PASSWORD}Adding Actual Passwords (Custom kafka-mirrormaker2)
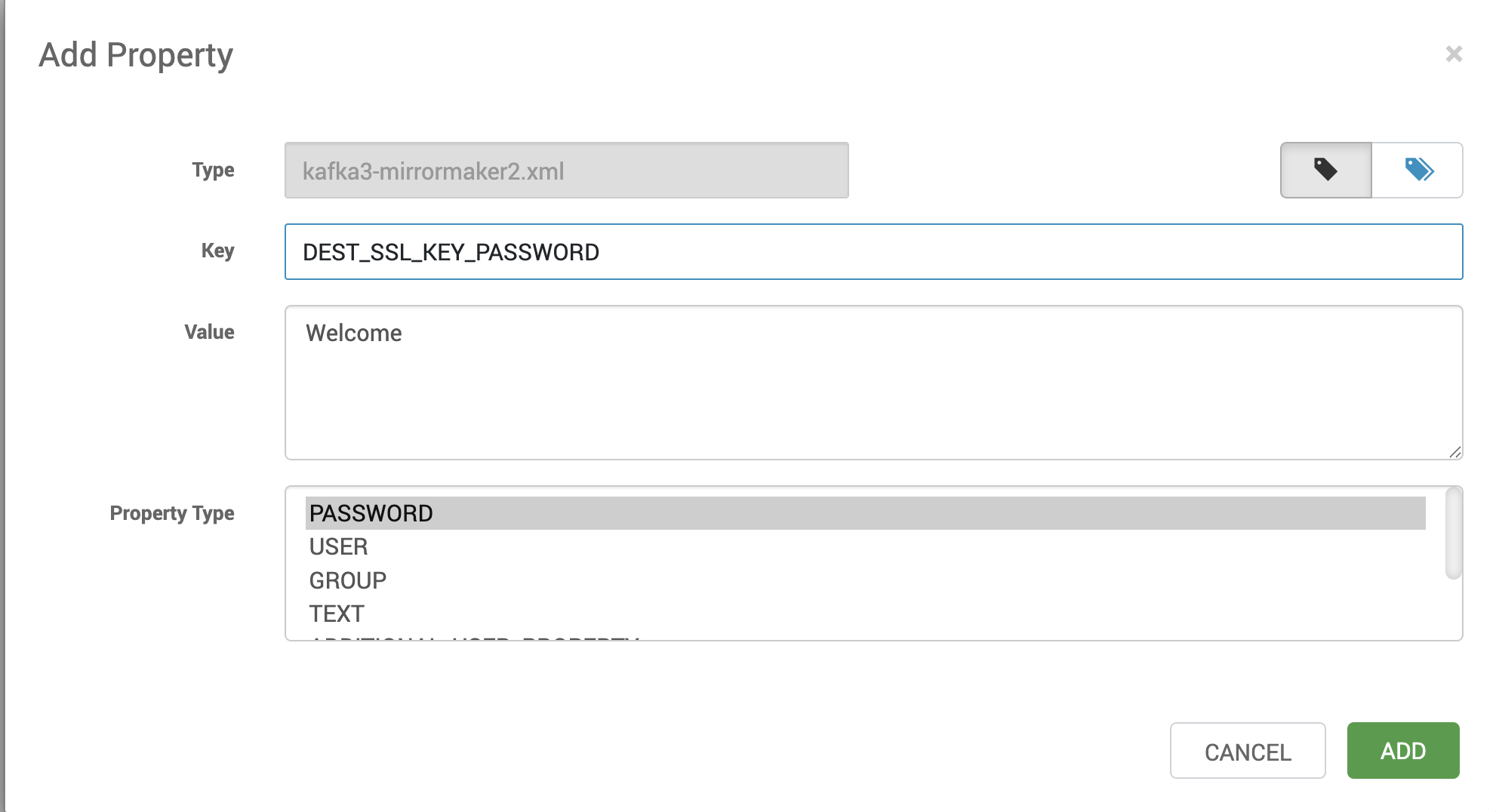
- Provide the real password values in Custom kafka-mirrormaker2 using secure variables.
- This ensures that no plaintext passwords are exposed in Ambari configuration files.
Kafka 3 Mirror Maker
- All configurations must be provided under Advanced kafka3-mirrormaker2 in Ambari.
- Any property ending with .password must reference an environment variable instead of storing the password directly.
Example Configuration (Advanced kafka3-mirrormaker2)
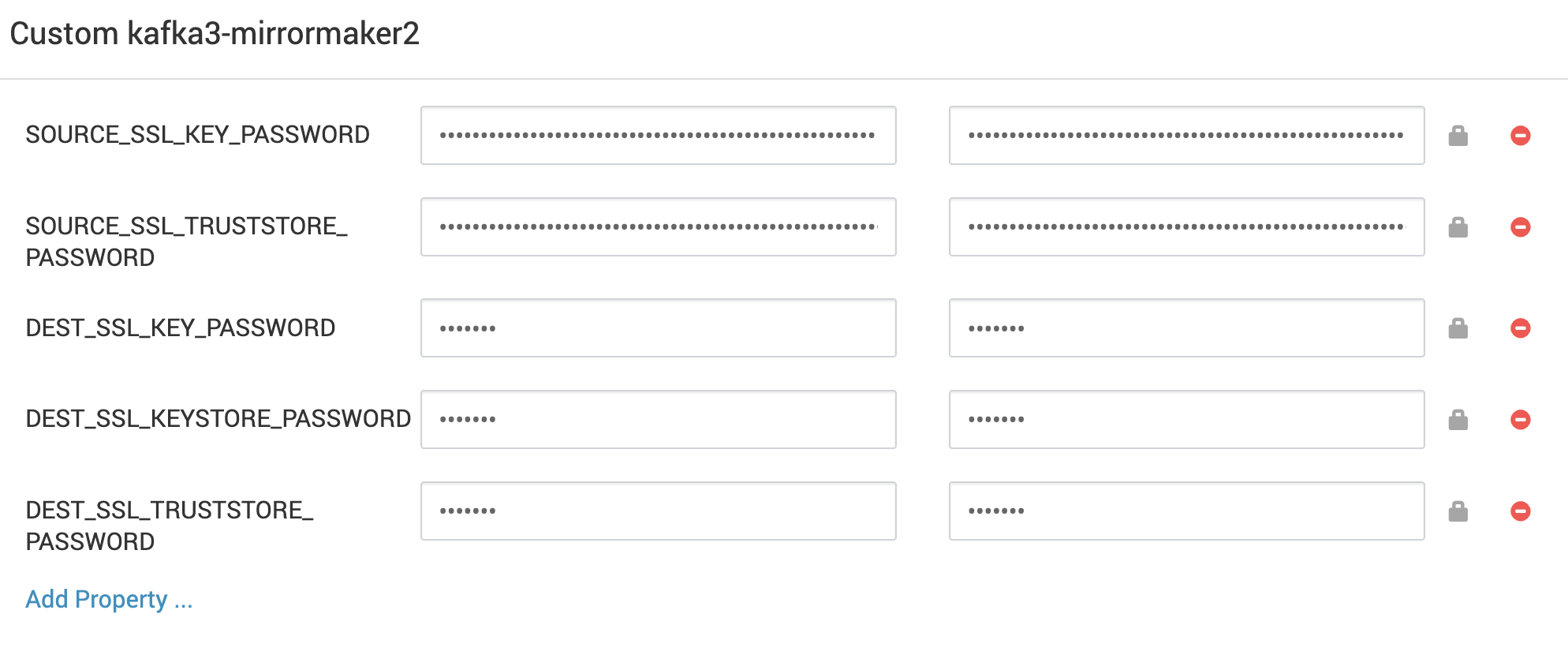
source.ssl.key.password=${env:SOURCE_SSL_KEY_PASSWORD}source.ssl.keystore.password=${env:SOURCE_SSL_KEYSTORE_PASSWORD}source.ssl.truststore.password=${env:SOURCE_SSL_TRUSTSTORE_PASSWORD}dest.ssl.key.password=${env:DEST_SSL_KEY_PASSWORD}dest.ssl.keystore.password=${env:DEST_SSL_KEYSTORE_PASSWORD}dest.ssl.truststore.password=${env:DEST_SSL_TRUSTSTORE_PASSWORD}Adding Actual Passwords (Custom kafka3-mirrormaker2)
- Provide the real password values in Custom kafka3-mirrormaker2 using secure variables.
- This approach prevents plaintext passwords from appearing in Ambari configuration files.
Impala
LDAP passwords are obfuscated using security_credential_helper.py.
Ozone
Update OBF in replace to plaintext passwords on Ambari UI
Generate an OBF Password
Run the following command:
[root@test15 certificates]# java -cp /usr/odp/3.3.6.3-1/hadoop/lib/jetty-util-9.4.57.v20241219.jar org.eclipse.jetty.util.security.Password <<PASSWORD>>2025-05-27 15:54:19.535:INFO::main: Logging initialized @94ms to org.eclipse.jetty.util.log.StdErrLog<<PASSWORD>>OBF:<< hash generated >>MD5:<< md5 hash >>Output includes:
- Plaintext password (for confirmation)
OBF:<<hash generated>>— obfuscated passwordMD5:<<md5 hash>>— hash representation
Oozie
- Previously, SSL passwords were displayed in the Ambari UI, even though they were encrypted in the configuration file system under oozie-site.jceks.
- These SSL passwords in the UI are now obfuscated.
Generate an OBF Password
Run the following command:
[root@test15 certificates]# java -cp /usr/odp/3.3.6.3-1/hadoop/lib/jetty-util-9.4.57.v20241219.jar org.eclipse.jetty.util.security.Password <<PASSWORD>>2025-05-27 15:54:19.535:INFO::main: Logging initialized @94ms to org.eclipse.jetty.util.log.StdErrLog<<PASSWORD>>OBF:<< hash generated >>MD5:<< md5 hash >>Output includes:
- Plaintext password (for confirmation)
OBF:<<hash generated>>— obfuscated passwordMD5:<<md5 hash>>— hash representation
Example:oozie-site.xml
[root@vars17-rl8-0 conf]# grep -ir OBFoozie-site.xml: <value>OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq</value>oozie-site.xml: <value>OBF:1dhw1i9a1inm1nse1x8e1x8g1nps1iks1i6o1dgq</value>