Title
Create new category
Edit page index title
Edit category
Edit link
Securing NiFi with CA Certificates
Securing NiFi with CA Certificates without NiFi LDAP authentication:
In this scenario, a commercial Certificate Authority (CA) is being used, although it could alternatively involve an enterprise CA that is equipped with an internal CA certificate that is set up to be trusted by corporate devices. Many commercial vendors provide signed certificates, and TinyCert is chosen here due to its no-cost nature. Another option, Let’s Encrypt, also offers free certificates but requires hostname ownership verification, which involves additional steps not detailed in this scenario.
All certificates and keys in this setup will follow the Privacy-Enhanced Mail (PEM) format, which is a widely accepted standard for certificates and keys. PEM uses Base64 encoding for file contents, allowing for seamless transmission across various mediums and storage systems. The contents can be easily viewed using plain text editors, while tools like openssl and keytool are capable of parsing them.
Example PEM file:
% cat nifi.pem-----BEGIN CERTIFICATE-----MIIFDzCCA/egAwIBAgICURswDQYJKoZIhvcNAQELBQAwgZMxCzAJBgNVBAYTAlVTMQswCQYDVQQIDAJDQTEVMBMGA1UEBwwMU2FudGEgTW9uaWNhMRcwFQYDVQQKDA5BcGFjaGUgTmlGaSBDQTErMCkGA1UECwwiU2VjdXJlIERpZ2l0YWwgQ2VydGlmaWNhdGUgU2lnbmluZzEaMBgGA1UEAwwRQXBhY2hlIE5pRmkgQ0EgQ0EwHhcNMjAwNDA1MjI0MTQ5WhcNMjEwNDA1MjI0MTQ5WjCBgjELMAkGA1UEBhMCVVMxCzAJBgNVBAgMAkNBMRUwEwYDVQQHDAxTYW50YSBNb25pY2ExFzAVBgNVBAoMDkFwYWNoZSBOaUZpIENBMSAwHgYDVQQLDBdBcGFjaGUgTmlGaSBXYWxrdGhyb3VnaDEUMBIGA1UEAwwLc2VjdXJlLm5pZmkwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDJySMXH+Fco7WbXIKQ1u1RrMd/FE7zl/69X/7Da6x4c6jlI8fy3MbxZjqFnDsJpNuIkPVvyHcGCm8Lkw70DbCTUkW60MlVM5r4CkWhVgOd1RD34QzhgkcKjg29uOuCYa+FM78qE5Qp64wbLpDXHpxmm4/Qv97RHdTqynqRzYs6g+VyCn14nXuqJp0533F1T2khtK4zBrIMZj6VpWyyCFmJjmrW37GbcRuxMbtbgj+4mzD0Eew6/96R9A7Wxlq0QMuRTz12ie9xSi/GyzQV2r9gRzxuIo8qshMIq2d/1pipIgWNj2LzEXXoEbfHy7Jwm78e1G/+PV/ULIx+QL4h9Ni/AgMBAAGjggF6MIIBdjAJBgNVHRMEAjAAMB0GA1UdDgQWBBTygw/GBUrqMI80gYpdlh3NNfwrBzAfBgNVHSMEGDAWgBRkovbp8RqbD0BeDyPcrBYga1rzdDARBglghkgBhvhCAQEEBAMCBPAwCwYDVR0PBAQDAgP4MDsGA1UdJQQ0MDIGCCsGAQUFBwMBBggrBgEFBQcDAgYIKwYBBQUHAwMGCCsGAQUFBwMEBggrBgEFBQcDCDBtBggrBgEFBQcBAQRhMF8wLAYIKwYBBQUHMAGGIGh0dHA6Ly9vY3NwLnRpbnljZXJ0Lm9yZy9jYS0yNDA1MC8GCCsGAQUFBzAChiNodHRwOi8vYWlhLnRpbnljZXJ0Lm9yZy9jYS0yNDA1LmNydDA0BgNVHR8ELTArMCmgJ6AlhiNodHRwOi8vY3JsLnRpbnljZXJ0Lm9yZy9jYS0yNDA1LmNybDAnBgNVHREEIDAeggtzZWN1cmUubmlmaYcEfwAAAYIJbG9jYWxob3N0MA0GCSqGSIb3DQEBCwUAA4IBAQDAICxyfgm2eBa8J3+sD2QpIQgOc8fgMYeqWwgk5rHbDk8IdkH9XloAuSzxi/weZt3PQQOdNHeeOCOXEWAfn0X1SMGFUvLForHgArGolt9uFofvh2sE2q3/wSBI6J2940dYwZOPAlf5m7fNpcbzWCJZGt7Pn/VWm3+uPZrMAj+GzsvR9NVMZwK/eAFM4OKNCeiLRPv1qLARYVqvLJFKt9dlCrHKyDLIaUbG2Lcw6Yt7SBU7nAnobuYqImRRXm/bE0xwb9X9fD8UzJfmryOTFvz4hlntwk1fgvG1n4SrZgFNZpg1awN5tXbwiOdisTwslQ49C4QCH5iEWCM1HExLA5GR-----END CERTIFICATE-----Example parsed contents:
% openssl x509 -in nifi.pem -text -nooutCertificate: Data: Version: 3 (0x2) Serial Number: 20763 (0x511b) Signature Algorithm: sha256WithRSAEncryption Issuer: C=US, ST=CA, L=Santa Monica, O=Apache NiFi CA, OU=Secure Digital Certificate Signing, CN=Apache NiFi CA CA Validity Not Before: Apr 5 22:41:49 2020 GMT Not After : Apr 5 22:41:49 2021 GMT Subject: C=US, ST=CA, L=Santa Monica, O=Apache NiFi CA, OU=Apache NiFi Walkthrough, CN=secure.nifi Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:c9:c9:23:17:1f:e1:5c:a3:b5:9b:5c:82:90:d6: ed:51:ac:c7:7f:14:4e:f3:97:fe:bd:5f:fe:c3:6b: ac:78:73:a8:e5:23:c7:f2:dc:c6:f1:66:3a:85:9c: 3b:09:a4:db:88:90:f5:6f:c8:77:06:0a:6f:0b:93: 0e:f4:0d:b0:93:52:45:ba:d0:c9:55:33:9a:f8:0a: 45:a1:56:03:9d:d5:10:f7:e1:0c:e1:82:47:0a:8e: 0d:bd:b8:eb:82:61:af:85:33:bf:2a:13:94:29:eb: 8c:1b:2e:90:d7:1e:9c:66:9b:8f:d0:bf:de:d1:1d: d4:ea:ca:7a:91:cd:8b:3a:83:e5:72:0a:7d:78:9d: 7b:aa:26:9d:39:df:71:75:4f:69:21:b4:ae:33:06: b2:0c:66:3e:95:a5:6c:b2:08:59:89:8e:6a:d6:df: b1:9b:71:1b:b1:31:bb:5b:82:3f:b8:9b:30:f4:11: ec:3a:ff:de:91:f4:0e:d6:c6:5a:b4:40:cb:91:4f: 3d:76:89:ef:71:4a:2f:c6:cb:34:15:da:bf:60:47: 3c:6e:22:8f:2a:b2:13:08:ab:67:7f:d6:98:a9:22: 05:8d:8f:62:f3:11:75:e8:11:b7:c7:cb:b2:70:9b: bf:1e:d4:6f:fe:3d:5f:d4:2c:8c:7e:40:be:21:f4: d8:bf Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: CA:FALSE X509v3 Subject Key Identifier: F2:83:0F:C6:05:4A:EA:30:8F:34:81:8A:5D:96:1D:CD:35:FC:2B:07 X509v3 Authority Key Identifier: keyid:64:A2:F6:E9:F1:1A:9B:0F:40:5E:0F:23:DC:AC:16:20:6B:5A:F3:74 Netscape Cert Type: SSL Client, SSL Server, S/MIME, Object Signing X509v3 Key Usage: Digital Signature, Non Repudiation, Key Encipherment, Data Encipherment, Key Agreement X509v3 Extended Key Usage: TLS Web Server Authentication, TLS Web Client Authentication, Code Signing, E-mail Protection, Time Stamping Authority Information Access: OCSP - URI:http://ocsp.tinycert.org/ca-2405 CA Issuers - URI:http://aia.tinycert.org/ca-2405.crt X509v3 CRL Distribution Points: Full Name: URI:http://crl.tinycert.org/ca-2405.crl X509v3 Subject Alternative Name: DNS:secure.nifi, IP Address:127.0.0.1, DNS:localhost Signature Algorithm: sha256WithRSAEncryption c0:20:2c:72:7e:09:b6:78:16:bc:27:7f:ac:0f:64:29:21:08: 0e:73:c7:e0:31:87:aa:5b:08:24:e6:b1:db:0e:4f:08:76:41: fd:5e:5a:00:b9:2c:f1:8b:fc:1e:66:dd:cf:41:03:9d:34:77: 9e:38:23:97:11:60:1f:9f:45:f5:48:c1:85:52:f2:c5:a2:b1: e0:02:b1:a8:96:df:6e:16:87:ef:87:6b:04:da:ad:ff:c1:20: 48:e8:9d:bd:e3:47:58:c1:93:8f:02:57:f9:9b:b7:cd:a5:c6: f3:58:22:59:1a:de:cf:9f:f5:56:9b:7f:ae:3d:9a:cc:02:3f: 86:ce:cb:d1:f4:d5:4c:67:02:bf:78:01:4c:e0:e2:8d:09:e8: 8b:44:fb:f5:a8:b0:11:61:5a:af:2c:91:4a:b7:d7:65:0a:b1: ca:c8:32:c8:69:46:c6:d8:b7:30:e9:8b:7b:48:15:3b:9c:09: e8:6e:e6:2a:22:64:51:5e:6f:db:13:4c:70:6f:d5:fd:7c:3f: 14:cc:97:e6:af:23:93:16:fc:f8:86:59:ed:c2:4d:5f:82:f1: b5:9f:84:ab:66:01:4d:66:98:35:6b:03:79:b5:76:f0:88:e7: 62:b1:3c:2c:95:0e:3d:0b:84:02:1f:98:84:58:23:35:1c:4c: 4b:03:91:91The prerequisites for this scenario, as issued by the IT department, include:
- A signed NiFi server certificate for the specified host (secure.nifi in this example) in PEM format (
nifi.pem) - The corresponding private key in PEM format (
nifi.key) - A signed client certificate for the specified user (
CN=my_username, etc. in this example) in PEM format (client.pem) - The corresponding private key in PEM format (
client.key) - The CA certificate in PEM format (
cacert.pem)
For more information on converting certificates between various formats, refer to the Toolkit Guide: Additional Certificate Commands.
The final setup will include a self-signed external CA (the root), a keystore and truststore containing the necessary certificates for the NiFi instance to operate, and a client certificate for a human user to access NiFi.
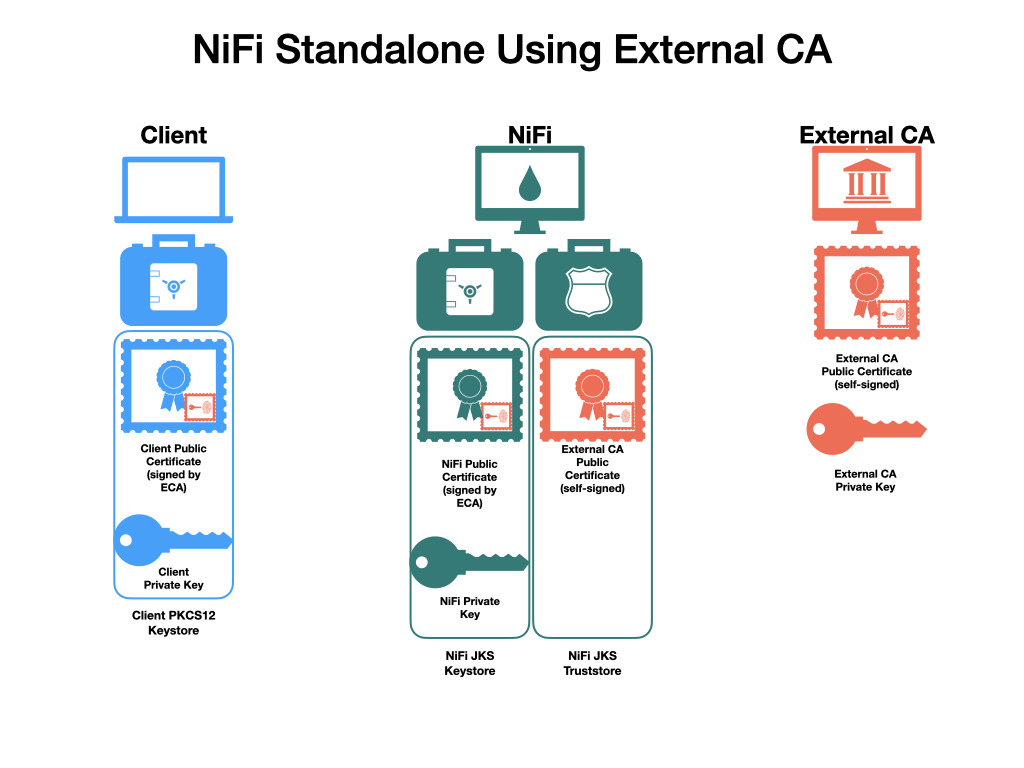
Certificate Requirements
Ensure compliance with the following certificate requirements, maintaining the sequence while shuffling the order:
The certificate's X509v3 ExtendedKeyUsages segment must include the following attributes:
- clientAuth: Intended for TLS web client authentication.
- serverAuth: Intended for TLS web server authentication.
Avoid the use of wildcard certificates. Each cluster node should have its own certificate. When NiFi or NiFi Registry operates behind Knox, do not use wildcard certificates for Knox.
The certificate's signature algorithm must use sha256WithRSAEncryption (SHA-256).
Subject Alternate Names (SANs) are mandatory and must include at least the Fully Qualified Domain Name (FQDN) of the host.
Additional names for the certificate/host can be added as SANs.
Include the FQDN used for the Common Name (CN) as a DNS SAN entry.
If considering the use of a load balancer for the NiFi service, include the FQDN of the load balancer as a DNS SAN entry.
The certificate's X509v3 KeyUsage segment should include the following attributes:
- DigitalSignature
- Key_Encipherment
The KeyStore should only contain a single PrivateKeyEntry. Using multiple private keys within one KeyStore is not recommended.
Ensure that the KeyStore password and the key/certificate password either match or are unset.
Consistency in KeyStore password and key/certificate password is crucial across all different KeyStores used on each NiFi cluster node. Individual passwords for NiFi hosts are not supported by Ambari.
Generate keystore.jksand truststore.jks for NiFi Hosts:
- Determine if the server certificate (
nifi.pem) contains the complete certificate chain or just the server certificate. If the sequence-----BEGIN CERTIFICATE-----occurs only once, this is just the server certificate. If it occurs multiple times, the certificate chain is present. If the certificate chain is present, continue with Step 3. If it is not present, continue to Step 2.
cat nifi.pem # Prints the Base64-encoded contents- Concatenate the server certificate and CA certificate to form the certificate chain.
cat cacert.pem >> nifi.pem # Concatenates the CA certificate to the NiFi server certificate in the proper order- Form the PKCS12 keystore from the certificate chain and private key.
openssl pkcs12 -export -out nifi.p12 -inkey nifi.key -in nifi.pem -name nifi-keyGenerates the PKCS12 keystore containing the private key and certificate chain under the alias nifi-key. The command will prompt for an export password. Choose a secure password and enter it twice for confirmation.
keytool -list -v -keystore nifi.p12 # Verifies the contents of the PKCS12 keystore (optional)- Convert the PKCS12 keystore for the NiFi instance into the Java KeyStore file (
keystore.jks). PKCS12 keystores are usable by NiFi, but JKS format is handled more robustly and causes fewer edge cases. JKS keystores cannot be formed directly from PEM files, so the PKCS12 keystore serves as an intermediate form.
keytool -importkeystore -srckeystore nifi.p12 -srcstoretype pkcs12 -srcalias nifi-key -destkeystore keystore.jks -deststoretype jks -destalias nifi-keyConverts the PKCS12 keystore to a JKS keystore. This command will prompt for a new keystore password twice, then prompt for the password set on the PKCS12 keystore from the previous step.
- Convert the CA certificate into the NiFi truststore (
truststore.jks) to allow trusted incoming connections.
keytool -importcert -alias nifi-cert -file cacert.pem -keystore truststore.jksImports the CA certificate into the truststore. This command will prompt for a new truststore password twice.
- Optionally, move the
keystore.jksandtruststore.jksfiles into theconf/directory. This step is not required but helps with organization. - Generate client certificates and add them to the machine browser to access the NiFi UI.
Generate the client certificate keystore from the client certificate and key.
openssl pkcs12 -export -out CN=my_username.p12 -inkey client.key -in client.pemCreates the PKCS12 keystore containing the client certificate and private key. This command prompts for an export password twice.
From this point, the instructions are identical to those using the TLS Toolkit, starting at Loading the client certificate in the browser.
Enable SSL with Existing Certificates (Using Ranger for Authorization)
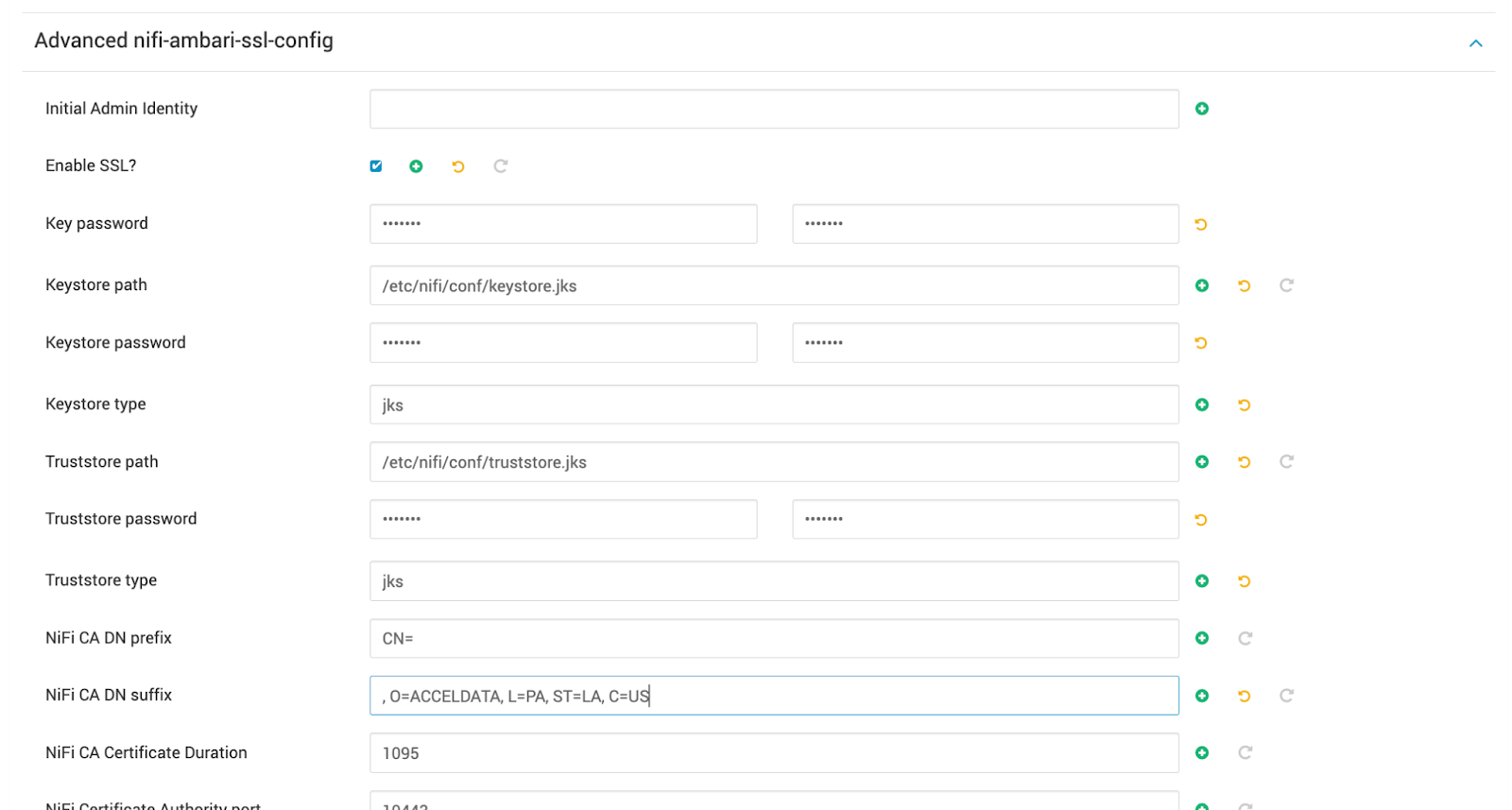
Navigate to Ambari UI > NiFi > Configs > Advanced > Advanced nifi-ambari-ssl-config and check the Enable SSL? box.
Configure the following values:
- Keystore path:
/etc/nifi/conf/keystore.jks - Keystore password
- Keystore type
- Keystore path:
Configure the following values:
- Truststore path:
/etc/nifi/conf/truststore.jks - Truststore password
- Truststore type
- Truststore path:
Setting Up Identity Mapping
Identity mapping properties can be configured to standardize user identities across different authentication methods in NiFi. Once set up, NiFi treats identities authenticated by various identity providers (such as certificates, LDAP, Kerberos) uniformly. This helps avoid creating duplicate users and ensures that user-specific configurations, such as authorizations, only need to be set up once per user.
Perform the following steps:
- Navigate to the NiFi service Configs tab and click on Advanced nifi-properties.
- Use the Filter box to search for
nifi.security.identity.mapping.pattern. - Enter the following values:
| Field | Sample Value |
|---|---|
| nifi.security.identity.mapping.pattern.dn | ^CN=(.*?), OU=(.*?)$ |
| nifi.security.identity.mapping.value.dn | $1@$2 |
| nifi.security.identity.mapping.pattern.kerb | ^(.*?)/instance@(.*?)$ |
| nifi.security.identity.mapping.value.kerb | $1@$2 |
- Click Save.
- Restart NiFi using the "Restart all Required" option from the Action menu.
Example
The following examples demonstrate normalizing Distinguished Names (DNs) from certificates and principals from Kerberos:
nifi.security.identity.mapping.pattern.dn=^CN=(.*?), OU=(.*?), O=(.*?), L=(.*?), ST=(.*?), C=(.*?)$nifi.security.identity.mapping.value.dn=$1@$2nifi.security.identity.mapping.pattern.kerb=^(.*?)/instance@(.*?)$nifi.security.identity.mapping.value.kerb=$1@$2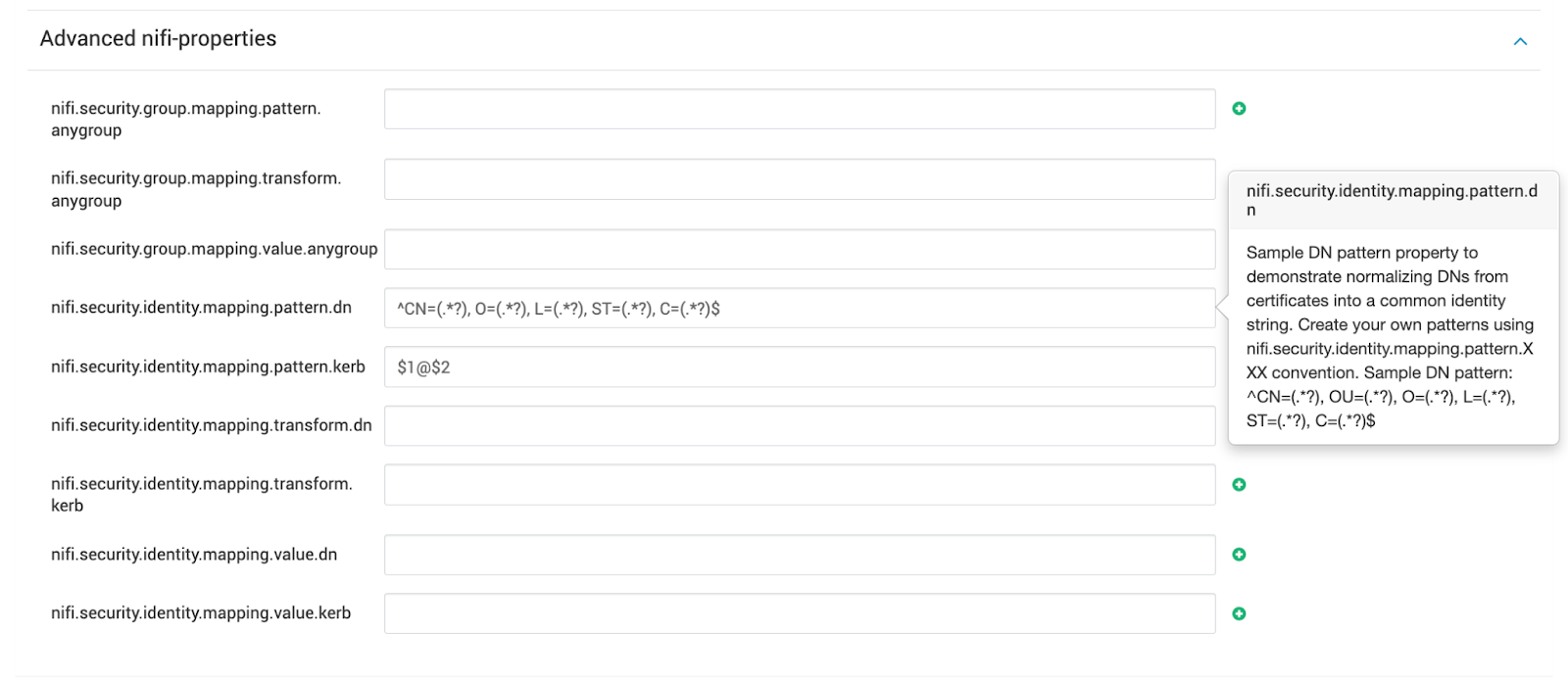
Logging into NiFi After Enabling SSL
After enabling SSL in NiFi, follow these steps to securely log in:
- Open NiFi from the Ambari Quick Links menu.
- When prompted by your browser, select the certificate you recently imported. Use incognito mode if the certificate prompt does not appear.
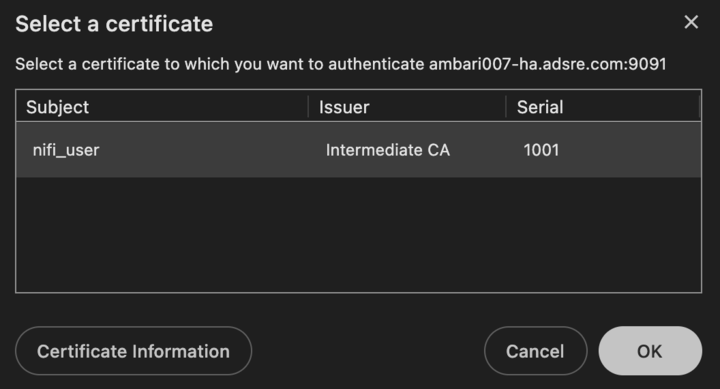
https://<local-host>:9091/nifi.
Additional Steps
- Ranger Test Connection Failure Due to SSL:
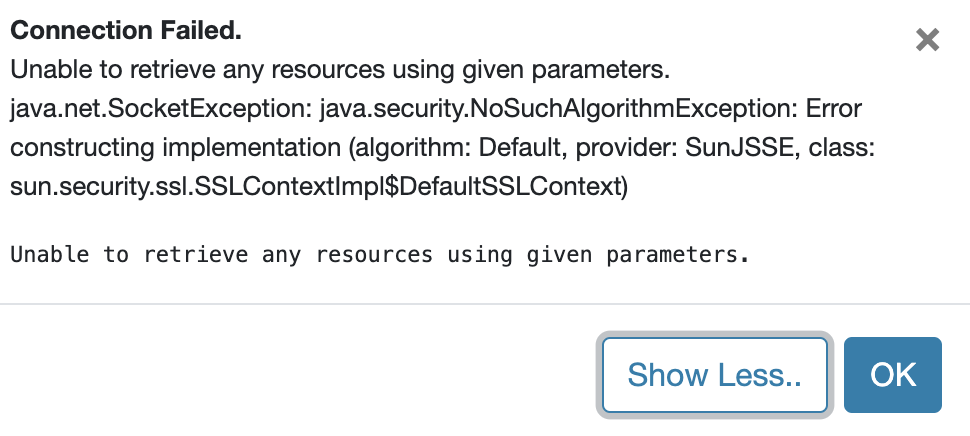
→ Configurations to Review: Log into the Ranger UI -> Edit NiFi Service Repo, and review the following:
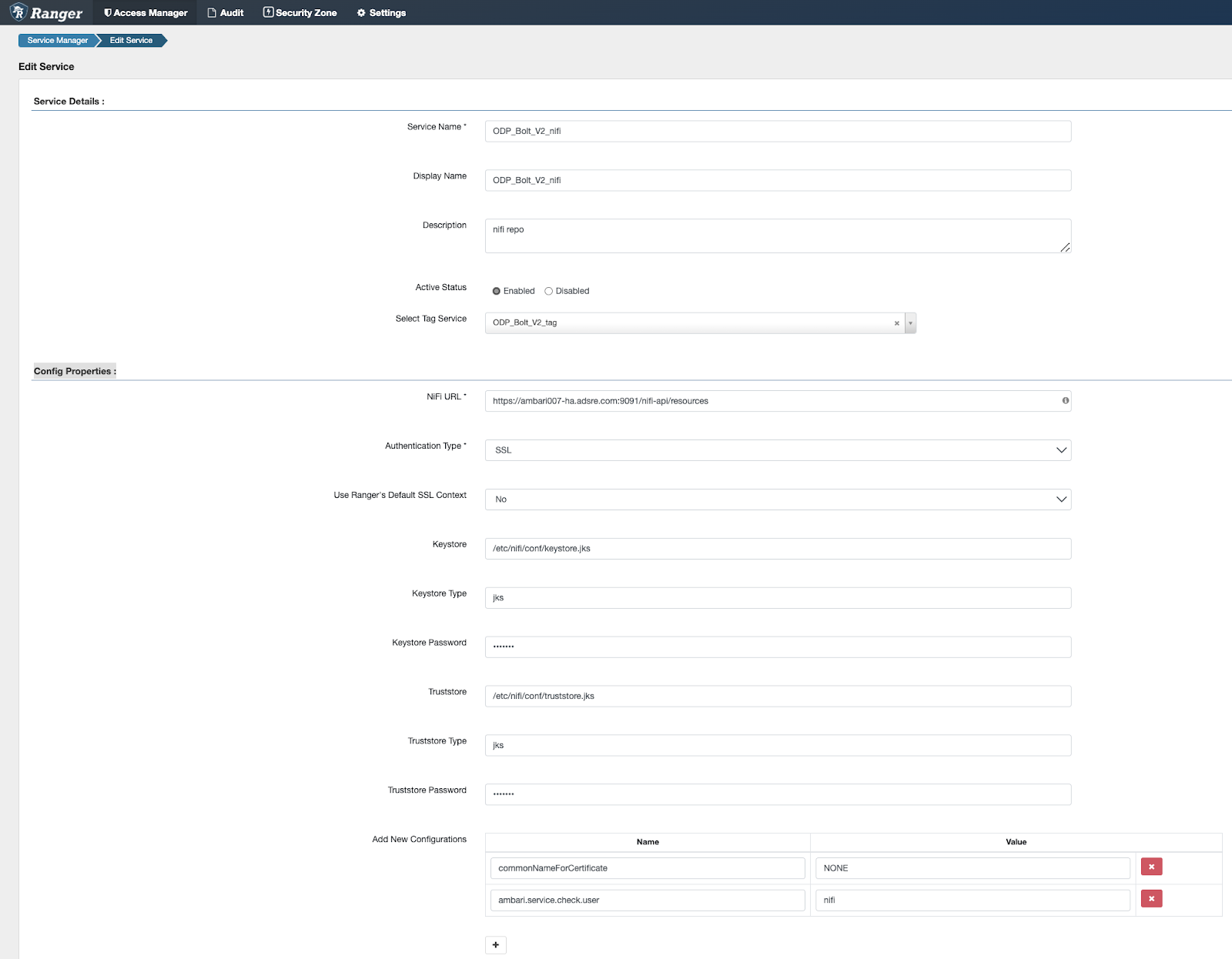
- NiFi URL
- Ensure that the Config Properties"are added or updated correctly.
- Ranger Test Connection Failure Due to 403 Forbidden Permission:
→ Review NiFi nifi-user.log
tailf /var/log/nifi/nifi-user.log<Rerun the Ranger NiFi Test connection>2024-05-09 19:04:27,916 INFO [NiFi Web Server-115] o.a.n.w.s.NiFiAuthenticationFilter Authentication Started 10.90.9.67 [CN=ambari007-ha.adsre.com, O=ACCELDATA, L=PA, ST=LA, C=US] GET https://ambari007-ha.adsre.com:9091/nifi-api/resources2024-05-09 19:04:27,916 INFO [NiFi Web Server-115] o.a.n.w.s.NiFiAuthenticationFilter Authentication Success [CN=ambari007-ha.adsre.com, O=ACCELDATA, L=PA, ST=LA, C=US] 10.90.9.67 GET https://ambari007-ha.adsre.com:9091/nifi-api/resources2024-05-09 19:04:27,924 INFO [NiFi Web Server-115] o.a.n.w.a.c.AccessDeniedExceptionMapper identity[CN=ambari007-ha.adsre.com, O=ACCELDATA, L=PA, ST=LA, C=US], groups[none] does not have permission to access the requested resource. No applicable policies could be found. Returning Forbidden response.Solution: Add Complete Certificate DN in Ranger User section and Add to Respective NiFi Policy.
Example: [CN=ambari007-ha.adsre.com, O=ACCELDATA, L=PA, ST=LA, C=US]
- Log into Ranger UI > Settings > Users > Add New User > Update User Name and New Password (dummy password, Meets password requirement) > Save it.
- Go to Ranger NiFi Policy → Add user to existing Policy or Create new One: Add new Policy Example:
NiFi Resource Identifier = /*Select User = [CN=ambari007-ha.adsre.com, O=ACCELDATA, L=PA, ST=LA, C=US]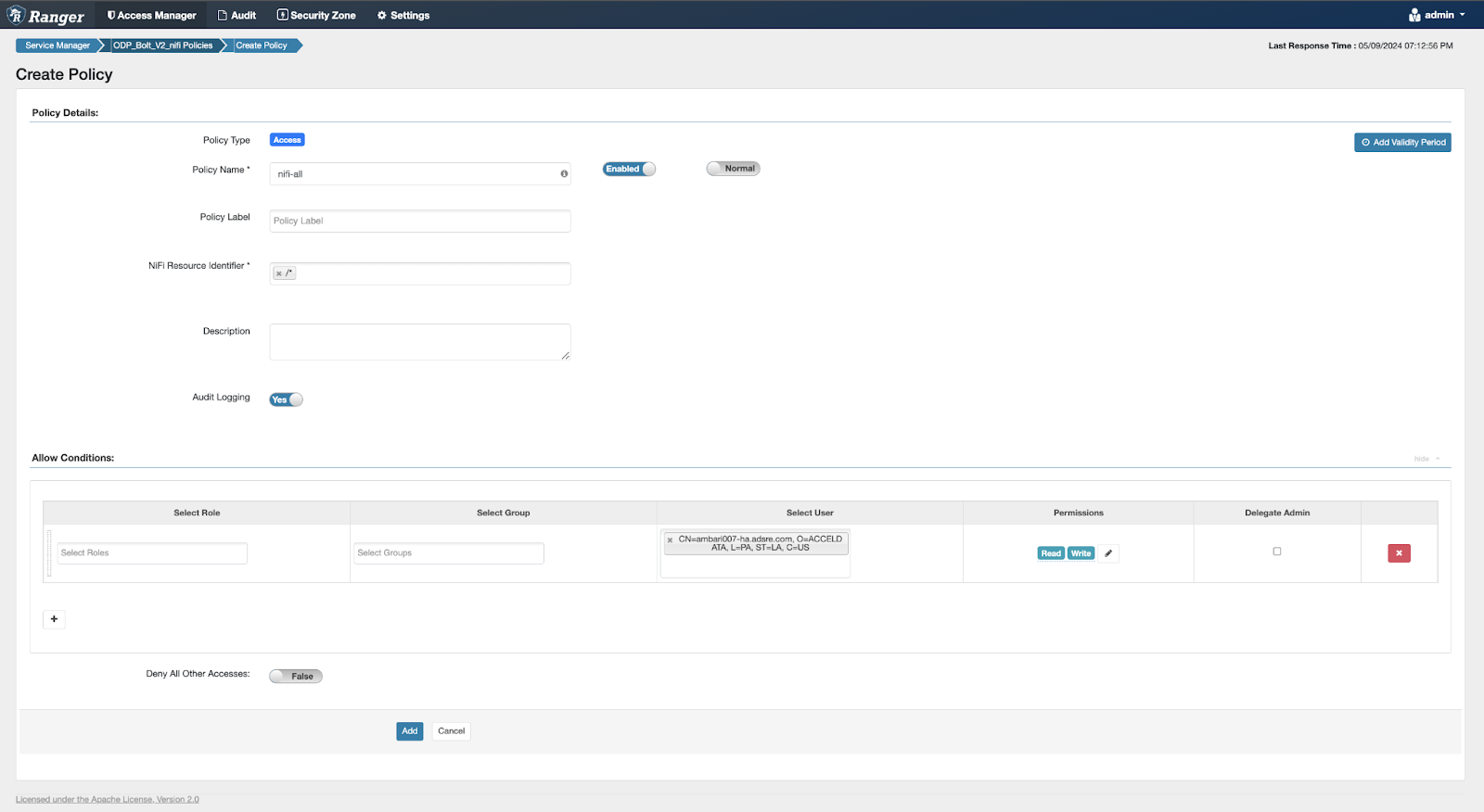
- Insufficient Permission | No applicable policy could be found:
→ Review NiFi Ranger Audits
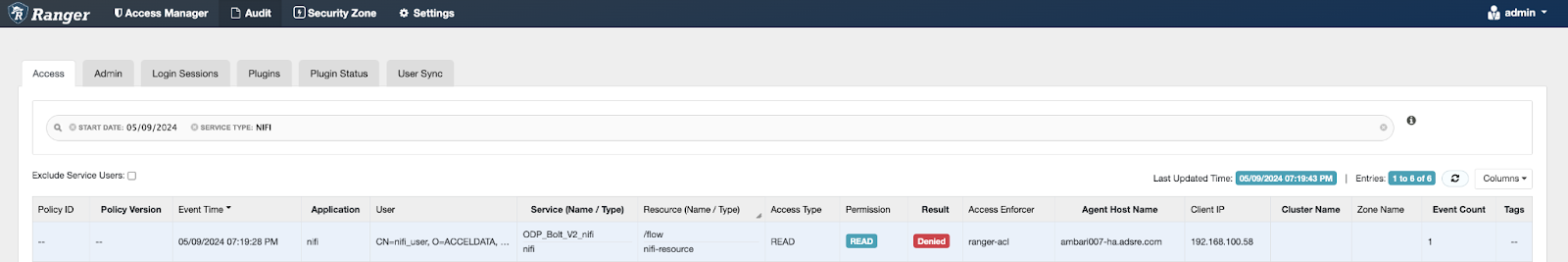
Solution: Add a Ranger policy for the client certificate.
User: CN=nifi_user, O=ACCELDATA, L=PA, ST=LA, C=US
Add user
CN=nifi_user, O=ACCELDATA, L=PA, ST=LA, C=USin Ranger:- Log into Ranger UI > Settings > Users > Add New User
- Update User Name and New Password (dummy password, meets password requirements).
- Save it.
Go to Ranger NiFi Policy > Add user to an existing policy or create a new one: Add new Policy Example:
NiFi Resource Identifier = /flowSelect User = CN=nifi_user, O=ACCELDATA, L=PA, ST=LA, C=US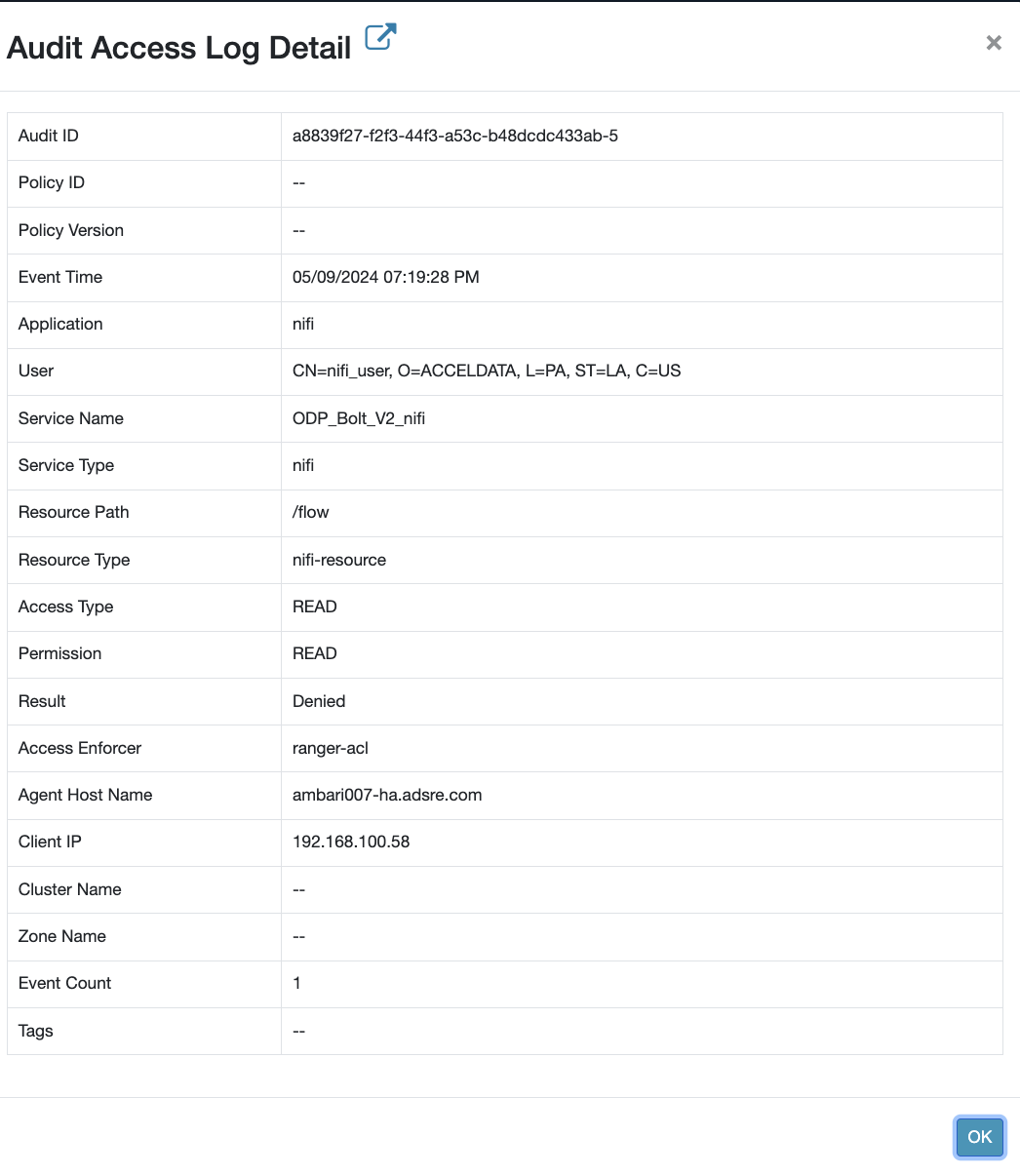
Enable SSL with Existing Certificates (Without Using Ranger for Authorization)
Check the Enable SSL? checkbox.
Specify the following values for Keystore path, Keystore password, and Keystore type:
- Keystore path:
/etc/nifi/conf/keystore.jks - Keystore password
- Keystore type
- Keystore path:
Set the Truststore path, Truststore password, and Truststore type:
- Truststore path:
/etc/nifi/conf/truststore.jks - Truststore password
- Truststore type
- Truststore path:
Provide the Initial Admin Identity details.
- The Initial Admin Identity represents the first administrator, enabling access to the UI and the ability to create additional users, groups, and policies. This information is mandatory unless you are using the Ranger plugin for NiFi authorization.
- Format for the Initial Admin Identity:
CN=admin, OU=NIFI. After adding the Initial Admin Identity, it is necessary to promptly generate a certificate for this user.
Define the Node Identities.
Specify the identity of each node in the NiFi cluster to facilitate communication between clustered nodes. This information is compulsory unless you are using the Ranger plugin for NiFi authorization.
Example:
<property name="Node Identity 1">CN=node1.fqdn, OU=NIFI</property><property name="Node Identity 2">CN=node2.fqdn, OU=NIFI</property><property name="Node Identity 3">CN=node3.fqdn, OU=NIFI</property>- Replace
node1.fqdn,node2.fqdn, andnode3.fqdnwith their respective fully qualified domain names.