GCS Secret Manager
Google Cloud Secret Manager is a secrets management service that helps you protect access to your applications, services, and IT resources. This service enables you to easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle. We are enabling ADOC to make use of Google Cloud Secrets Manager to store your secrets.
How to Create Secrets in Google Cloud?
- Login to your Google Cloud account.
- Search for Secrets Manager.
- Click Create Secret.
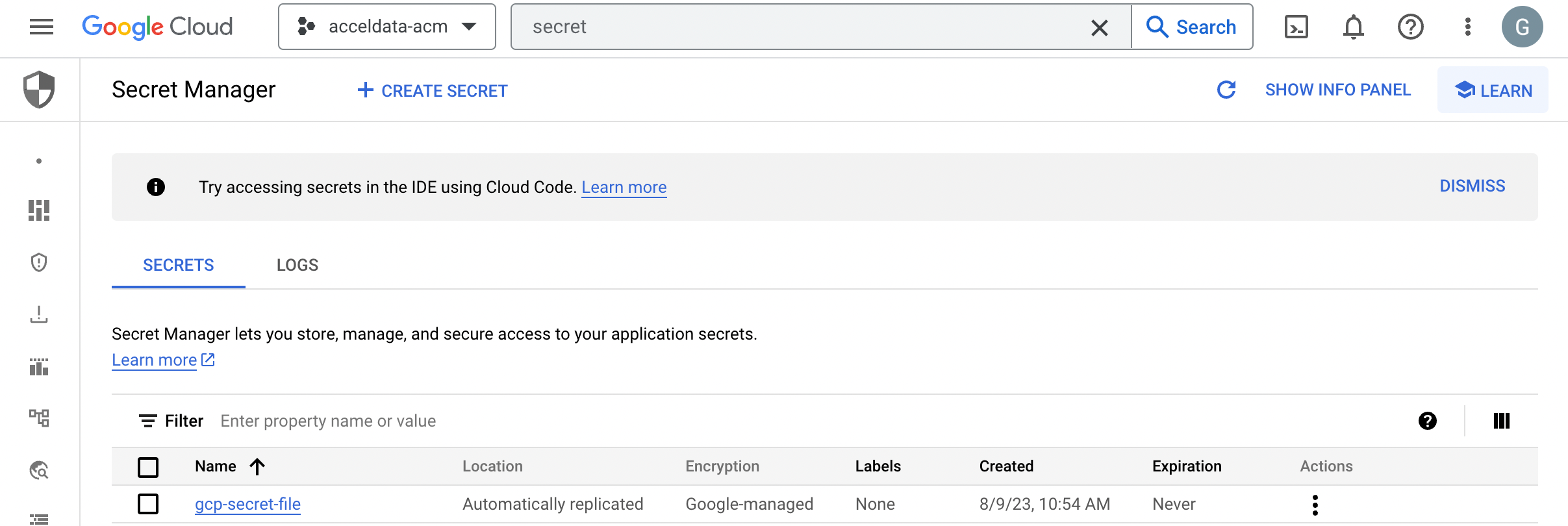
- Create a secret with a suitable name and a value representing the actual secret value like a password of a database user. You can also upload Files as a secret value in Google Cloud Secret Manager.
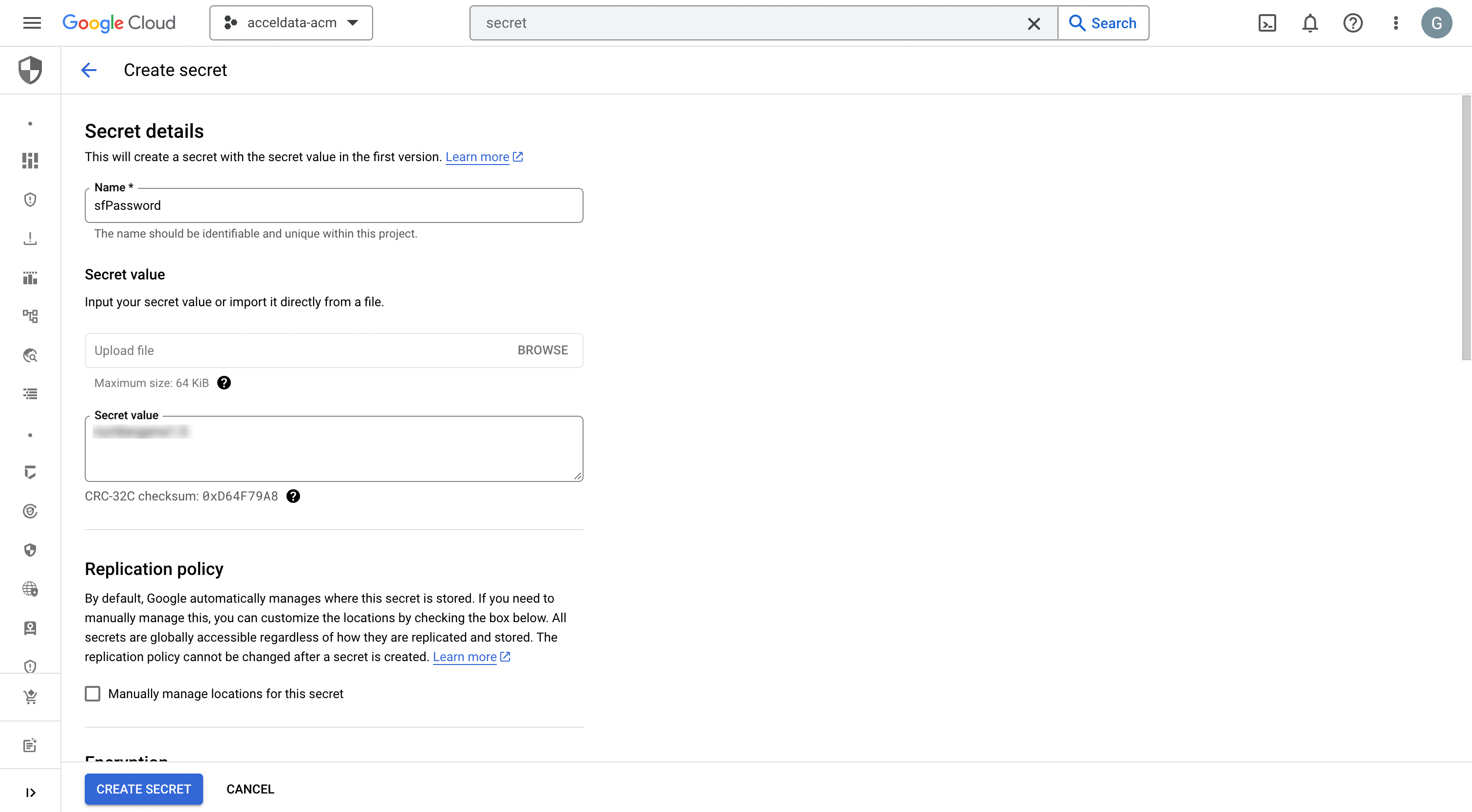
- Click the Create Secret button to create your secret.
How to Enable ADOC to Read from GCS Manager?
Perform the following steps to enable ADOC to read from Google Cloud Secret Manager:
- While deploying data plane make sure that we mount a secret manager configuration file on the analysis service
- A sample Secret Manager Configuration File for using Google Cloud Secrets Manager Service would look like the below code:
[ { "name": "jeevan-gcp", "type": "GCP_SECRETS_MANAGER", "details": { "credentialsFile": "/Users/jeevanpaul/Desktop/NPS/shubham-bigquery.json", "projectId": "acceldata-acm" } }]The Configuration file will create a Json Array, with each element representing a Secret Configuration.
There are two ways in which ADOC can authenticate itself to Google Cloud Secrets Manager.
- Populate the
credentialsFileproperty with a path, which represents the path at which the Service Account Credentials is mounted. - Leave the
credentialsFileas empty and ADOC assumes that there is an Identity Federation setup on this instance by which you can grant on-premises or multi-cloud workloads access to Google Cloud resources without using a service account.
- Populate the
Attach the following roles and permissions to the service account for authentication: Access Control with IAM.