Title
Create new category
Edit page index title
Edit category
Edit link
Configuring Ranger Admin and Usersync with SSSD or Centrify
This document provides detailed guidance for configuring the Apache Ranger Admin UI authentication using PAM with either SSSD or Centrify and setting up Ranger Usersync to synchronize users and groups from these services. The page includes step-by-step instructions, backup recommendations, troubleshooting tips, and an overview of limitations and known issues to ensure a smooth and secure configuration.
Introduction
Apache Ranger provides a centralized framework for managing fine-grained access control and auditing across the Hadoop ecosystem. Integrating Ranger with enterprise authentication systems like SSSD or Centrify enhances security by leveraging the existing user and group management. This document outlines the professional approach to configuration:
- Ranger Admin UI Authentication using PAM with SSSD or Centrify.
- Ranger Usersync to synchronize users and groups from SSSD or Centrify into Ranger.
Prerequisites
Before proceeding, ensure the following prerequisites are met:
- Administrative Access: You have administrative access to the system and Ambari UI.
- Ranger Components Installed: Apache Ranger Admin and Usersync services are installed and operational.
- SSSD or Centrify Configured: SSSD or Centrify is installed and properly configured to integrate with your directory services (e.g., Active Directory or LDAP).
- Backup Capability: Back up and restore the Ranger Admin database.
Configuring the Ranger Admin UI Authentication with PAM
Configuring the Ranger Admin to authenticate via PAM allows integration with system authentication services like SSSD or Centrify. This enables centralized user management and enhances security.
Using SSSD
Configure PAM Authentication in Ranger Admin:
- Access the Ambari Ranger Settings: Navigate to Ambari UI > Ranger > Configs > Advanced > Ranger Settings.
- Set the Authentication Method to PAM: Locate the Authentication method setting and select PAM from the dropdown menu.
- Save Configuration and Restart Ranger:
- Click Save to apply the changes.
- Restart the Ranger Admin service to activate the new authentication method.
Modify PAM Configuration for Ranger Admin:
- Locate the PAM Configuration File: The default PAM configuration file for Ranger Admin is
/etc/pam.d/ranger-admin. - Edit the PAM Configuration File: Open
/etc/pam.d/ranger-adminwith a text editor (e.g., vi, nano).
- Locate the PAM Configuration File: The default PAM configuration file for Ranger Admin is
Ensure that the file contains the following configuration details:
#%PAM-1.0auth sufficient pam_unix.soauth sufficient pam_sss.soaccount sufficient pam_unix.soaccount sufficient pam_sss.soThis configuration allows authentication using both local UNIX accounts and SSSD-managed accounts.
c. Save and Secure the Configuration File: Save the changes and ensure that the file permissions restrict access appropriately (e.g., chmod 644 /etc/pam.d/ranger-admin).
Verify the SSSD Integration:
Test Authentication:
- Attempt to log in to the Ranger Admin UI using a user account managed by SSSD.
Check SSSD Service:
- Ensure the SSSD service is running: systemctl status sssd.
Review Logs if Necessary: Check
/var/log/sssd/for any authentication errors.
Using Centrify
Configure the PAM Authentication in Ranger Admin:
- Access the Ambari Ranger Settings: Navigate to Ambari UI > Ranger > Configs > Advanced > Ranger Settings.
- Set Authentication Method to PAM: Set the Authentication method to PAM.
- Save Configuration and Restart Ranger:
- Click Save.
- Restart the Ranger Admin service.
Modify the PAM Configuration for Ranger Admin:
- Locate the PAM Configuration File: The PAM configuration file is located at
/etc/pam.d/ranger-admin. - Edit the PAM Configuration File: Open the file with a text editor.
- Locate the PAM Configuration File: The PAM configuration file is located at
Modify it to use the Centrify PAM modules:
#%PAM-1.0auth sufficient pam_centrifydc.soaccount sufficient pam_centrifydc.soThis configuration directs PAM to use Centrify for authentication.
c. Save and Secure the Configuration File: Save your changes and set appropriate permissions on the file.
- Verify the Centrify Integration:
- Test Authentication: Log in to the Ranger Admin UI using a Centrify-managed user account.
- Check the Centrify Services: Ensure the Centrify services are running properly.
- Review the Logs if Necessary: Examine the Centrify logs for any authentication issues.
Configuring Ranger Usersync with SSSD or Centrify
Ranger Usersync synchronizes user and group information from external sources into Ranger, facilitating consistent policy application.
Configuration steps:
Back up the Ranger Admin Database: Before making changes, ensure the following:
Backup Procedure:
- Use database-specific tools to back up the Ranger Admin database (e.g., mysqldump for MySQL).
- Verify the backup integrity.
Reason: Prevent data loss in case of unexpected synchronization issues, such as syncing a large number of unintended users.
Access Usersync Configuration in Ambari: Navigate to Ambari UI > Ranger > Configs > Usersync.
In the UserSync section, set Sync Source to UNIX.
This tells Usersync to pull user and group information from the local system accounts.
Configure NSS Backend:
- Navigate to Advanced > Custom ranger-ugsync-site.
- Add or update the property: ranger.usersync.unix.backend = nss
- This configures Usersync to use the NSS (Name Service Switch) backend, which works with SSSD or Centrify.
Save and Restart Usersync:
- Click Save to apply the configuration.
- Restart the Ranger Usersync service.
Verify the User and Group Synchronization.
Allow Synchronization Time: Wait a few minutes for the Usersync process to complete the initial synchronization.
Check Users and Groups in Ranger Admin UI:
- Log in to Ranger Admin UI.
- Navigate to Settings > Users/Groups.
- Verify that users and groups from SSSD or Centrify are listed.
Validate Group Memberships: Ensure that users are associated with the correct groups.
Limitations and Known Issues
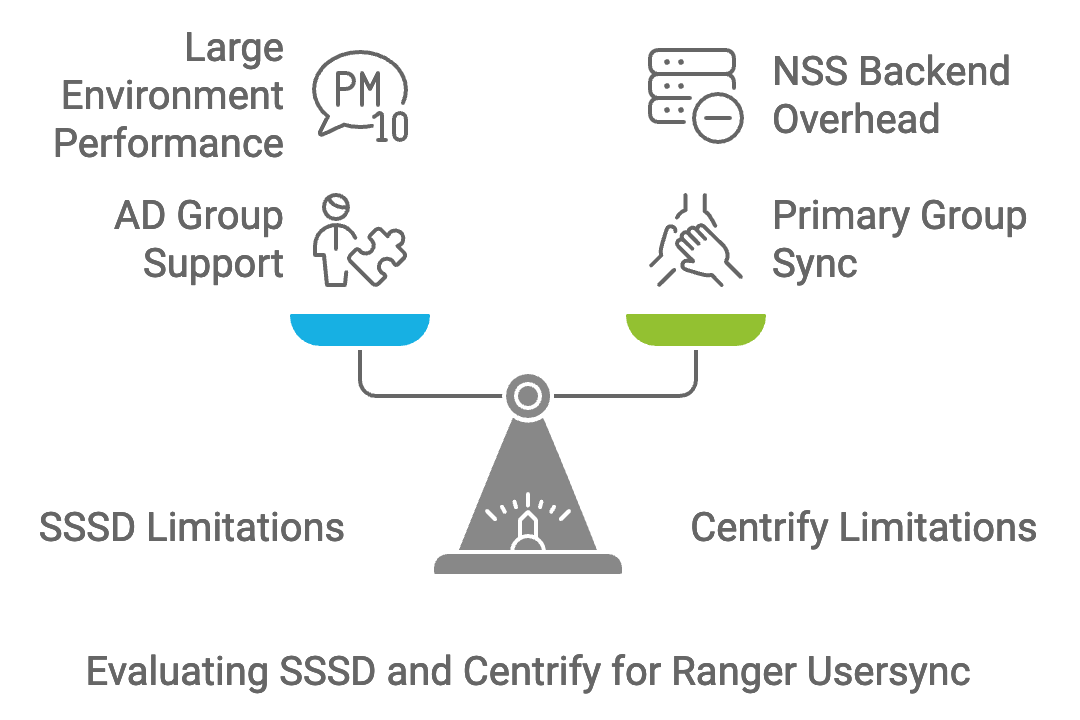
SSSD Limitations
Active Directory Group Types:
- Recommendation: Verify group compatibility and consider SSSD updates or configuration adjustments.
- SSSD may not support all AD group types (e.g., Universal, Global, Domain Local).
Large AD Environments:
- In environments with a large number of users/groups, SSSD might experience performance issues.
- Recommendation: Optimize SSSD caching and tune performance parameters.
Centrify Limitations
Primary Group Synchronization:
- Centrify may not synchronize a user's primary group as expected.
- Recommendation: Configure Ranger Usersync to handle primary groups explicitly or adjust Centrify settings. Validate via “getent group” cmd.
Performance in Large Environments:
- The NSS backend may introduce overhead, affecting performance.
- Recommendation: Evaluate performance impact and consider using direct LDAP/AD synchronization if necessary.
PAM Configuration Differences
Service Name Consistency
- The PAM service name in the Ranger configuration must match the PAM configuration file name.
- Recommendation: Ensure consistent naming (e.g., if the service is ranger-admin, the PAM file should be /etc/pam.d/ranger-admin).
Module-Specific Options:
- Some PAM modules require additional options or differ in syntax.
- Recommendation: Consult the documentation for pam_sss.so or pam_centrifydc.so for module-specific parameters.
Backup Recommendations
Regular backups are crucial for data integrity and disaster recovery.
Database Backups:
- Schedule regular backups of the Ranger Admin database.
- Use automated scripts where possible.
Configuration Backups:
- Export Ranger configuration settings regularly.
- Keep versioned copies to track changes over time.
Pre-Change Backups:
- Always perform a backup before significant changes, such as major updates or synchronization configuration adjustments.
Verification Steps
The post-configuration verification ensures that the setup is functioning as intended.
Ranger Admin UI Authentication
- Login Test:
- Attempt to log in to the Ranger Admin UI using a user authenticated via SSSD or Centrify.
- Confirm successful access without errors.
**
User Sync Verification
**
- User Listing:
- In Ranger Admin UI, navigate to Settings > Users/Groups. - Verify that the expected users are present.
- Group Membership:
- Check that users are correctly associated with their respective groups.
- Policy Application:
- Create a test policy and assign it to a synced group. - Validate that the policy is enforced for users in that group.
Troubleshooting
If issues arise during or after configuration, consider the following steps.
Authentication Issues
PAM Configuration Verification:
- Ensure that
/etc/pam.d/ranger-admincontains the correct module entries. - Check for syntax errors or missing modules.
- Ensure that
Service Status:
- Verify that SSSD or Centrify services are active and running without errors.
Log Examination:
- Check the following logs for errors:
- PAM authentication logs (e.g.,
/var/log/secure or /var/log/auth.log). - SSSD logs (
/var/log/sssd/sssd.logand domain-specific logs). - Centrify logs (e.g.,
/var/log/centrifydc.log).
- PAM authentication logs (e.g.,
- Check the following logs for errors:
Usersync Issues
Usersync Service Status:
- Confirm that the Ranger Usersync service is running:
Usersync Logs:
- Examine Usersync logs, typically located at
/var/log/ranger/usersync/usersync.log, for error messages.
- Examine Usersync logs, typically located at
NSS Configuration:
- Ensure that NSS is properly configured to retrieve user and group information from SSSD or Centrify.
- Check
/etc/nsswitch.conffor correct entries.
Performance Issues
Resource Utilization:
- Monitor CPU and memory usage during synchronization.
- Adjust system resources if necessary.
Configuration Tuning:
- Optimize SSSD or Centrify settings for performance.
- Consider limiting the scope of synchronization to necessary users and groups.
Conclusion
By following this professional guide, you have configured the Apache Ranger Admin UI authentication using PAM with SSSD or Centrify and set up Ranger Usersync to synchronize users and groups. This integration leverages existing authentication infrastructures, providing centralized and secure access control across your Hadoop ecosystem.
Regular monitoring, backups, and adherence to best practices will ensure a robust and reliable Ranger deployment, enhancing security compliance and operational efficiency.
Ensure all configurations comply with your organization's security policies and standards. Unauthorized changes may lead to security vulnerabilities or service disruptions.