Title
Create new category
Edit page index title
Edit category
Edit link
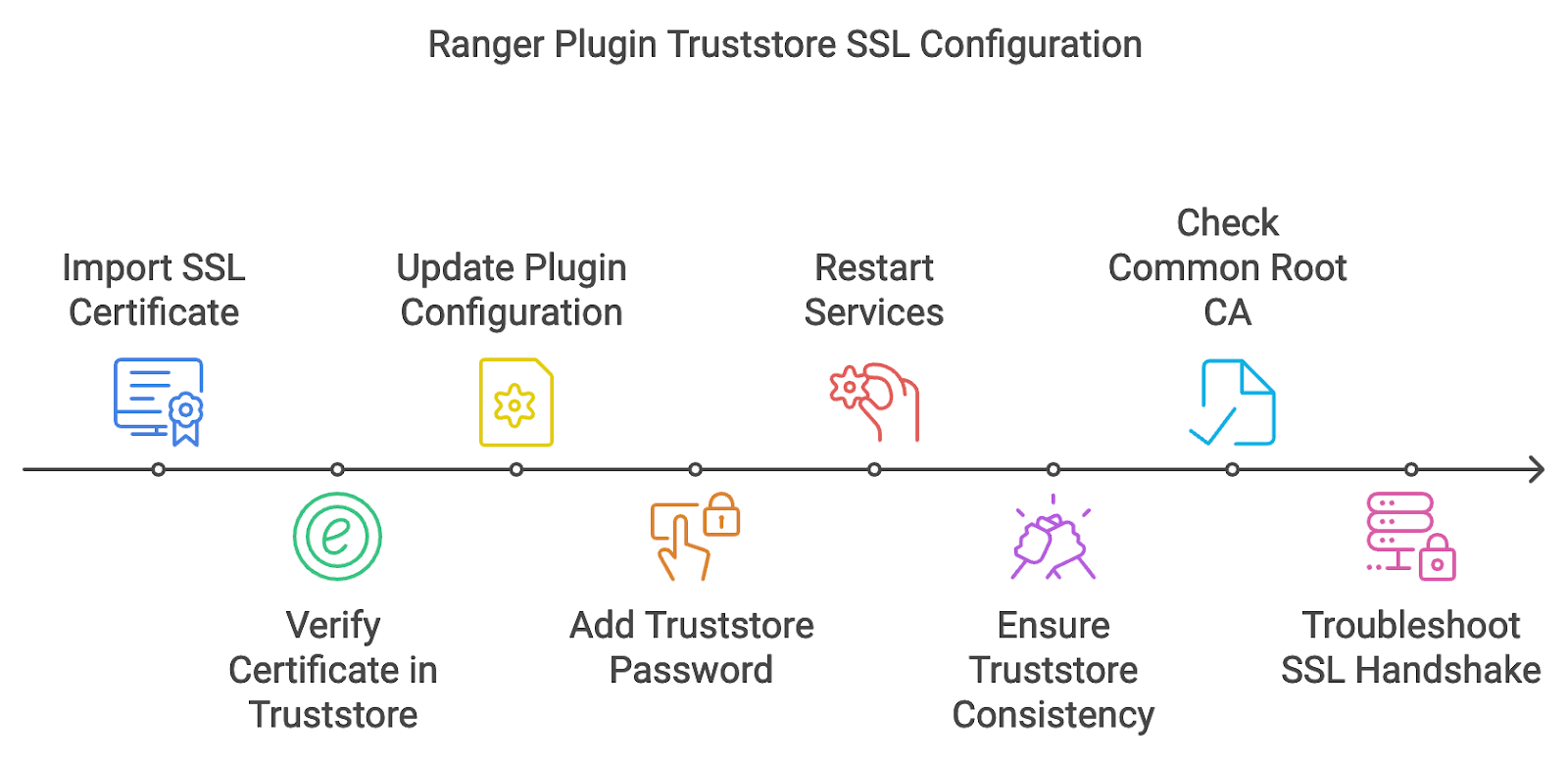
Configure the Ranger Plugin Truststore SSL
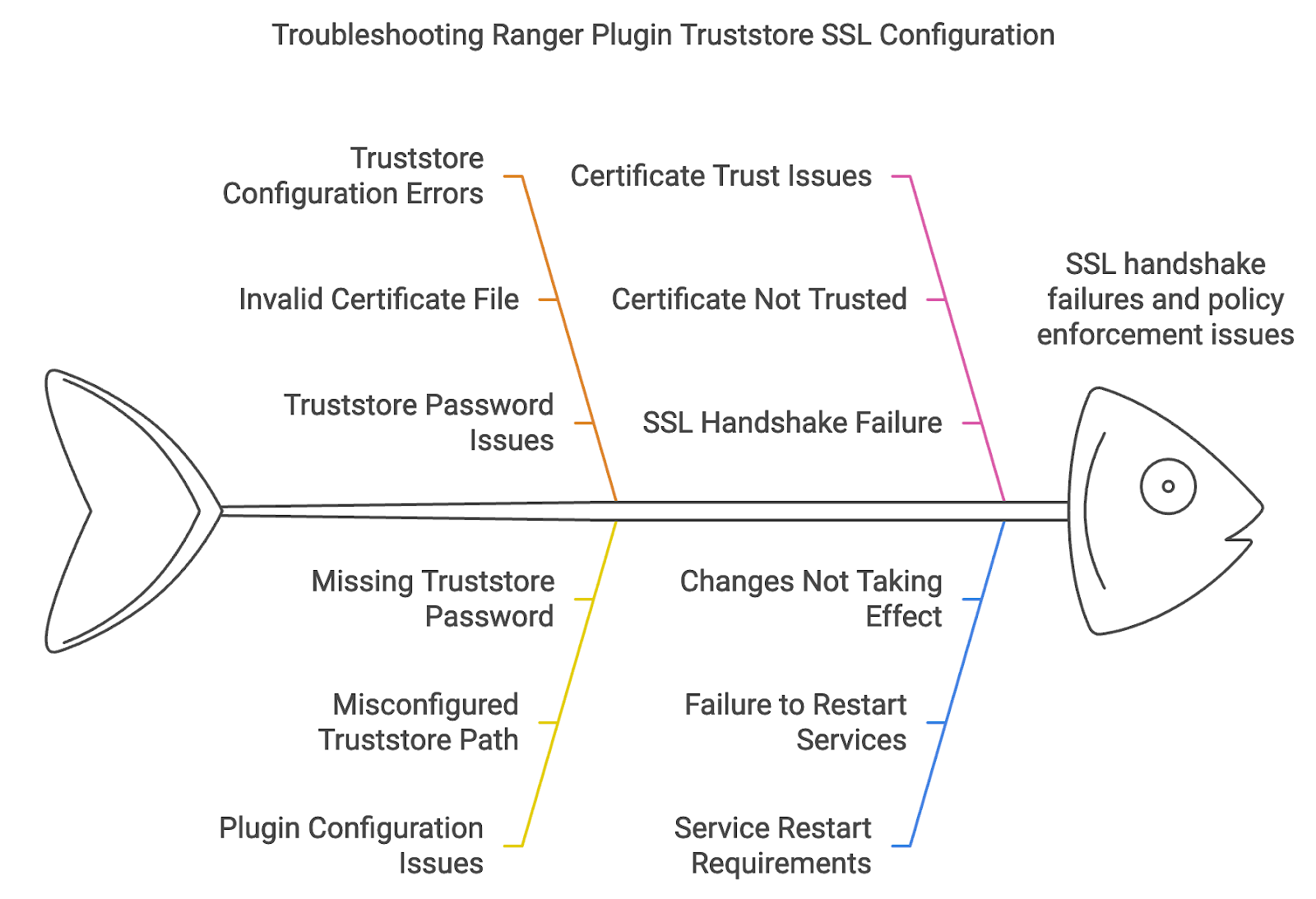
When setting up Ranger Plugin SSL configuration for services (such as HDFS, Hive, or YARN), it is crucial to properly configure the truststore to ensure secure communication between the Ranger service and plugins. Misconfigurations in truststore setups can lead to failures in policy enforcement and communication errors. Follow these steps to troubleshoot and debug issues with the Ranger Plugin Truststore SSL configuration.
Import the SSL Certificate of the Ranger Service into the Plugin Truststore
To establish secure communication, the SSL certificate of the Ranger service must be imported into the respective service’s (e.g., HDFS, Hive, YARN) plugin truststore.
- Import the Ranger Service Certificate: Use the keytool command to import the SSL certificate of the Ranger service into the truststore of the service plugin (e.g., HDFS plugin):
- -alias ranger: This is the alias for the certificate.
- -file /path/to/ranger_cert.pem: Path to the SSL certificate file of the Ranger service.
- -keystore /path/to/plugin-truststore.jks: Path to the plugin truststore (e.g., HDFS plugin truststore).
keytool -import -alias ranger -file /path/to/ranger_cert.pem -keystore /path/to/plugin-truststore.jksTroubleshooting:
- ** Invalid Certificate File: Ensure the certificate file exists and is correctly specified. If the certificate is in a different format (like .crt), you may need to convert it to the .pem format using OpenSSL.
- *
openssl x509 -in ranger_cert.crt -out ranger_cert.pem -outform PEM- Truststore Password Issues: If the truststore password is incorrect, keytool will fail to update the truststore. Make sure you use the correct password for the truststore.
- Verify the Certificate in the Truststore: After importing the certificate, verify that it has been added to the truststore.
keytool -list -keystore /path/to/plugin-truststore.jksThe output must show the certificate under the alias ranger. If the certificate is not listed, the import may have failed.
Update the Ranger Plugin Configuration to Use the Truststore
Each Hadoop service that uses the Ranger plugin (e.g., HDFS, Hive, YARN) must be configured to use the truststore containing the Ranger SSL certificate.
- Edit the Plugin Configuration File: Update the plugin’s configuration file (e.g., ranger-hdfs-plugin-properties for HDFS) to point to the truststore containing the Ranger certificate. Set the following property.
ranger.plugin.hdfs.policy.rest.ssl.config.truststore.file=/path/to/plugin-truststore.jksSimilar properties should be set for other services, such as Hive, YARN, etc.
- Add Truststore Password: Make sure to specify the truststore password in the configuration file.
ranger.plugin.hdfs.policy.rest.ssl.config.truststore.password=truststore-passwordTroubleshooting:
- Misconfigured Truststore Path: If the path to the truststore is incorrect or inaccessible, the service fails to load the truststore, resulting in SSL errors.
- Verify the path in the configuration file.
- Check if the truststore file exists and has the correct permissions.
Restart the Services: After updating the plugin configuration file, restart the respective service (e.g., HDFS, Hive) for the changes to take effect.
Ensure Truststore Consistency
For secure communication between the Ranger service and the Hadoop services, you need to ensure that the certificates are properly set in both the Ranger Plugin Truststore and the Ranger Service Truststore.
- Check the Ranger Service Truststore: If SSL is enabled for Ranger, verify that the Hadoop service certificate (e.g., HDFS, Hive) is imported into the Ranger Service truststore.
keytool -import -alias hdfs -file /path/to/hdfs_cert.pem -keystore /path/to/ranger-service-truststore.jksThis step is essential to ensure the Ranger service trusts the SSL certificates presented by the Hadoop services.
- Check Common Root CA (if applicable): If you are using a common Root CA for certificate issuance, make sure that the Root CA certificate is imported into both the service’s plugin truststore and the Ranger service’s truststore.
keytool -import -alias rootca -file /path/to/rootca_cert.pem -keystore /path/to/plugin-truststore.jkskeytool -import -alias rootca -file /path/to/rootca_cert.pem -keystore /path/to/ranger-service-truststore.jksA common Root CA helps eliminate issues arising from trust mismatches across services.
Troubleshooting:
- Certificate Not Trusted: If the certificate is not signed by a trusted CA (e.g., a self-signed certificate), ensure that the public key of the certificate is imported into both the truststores.
- SSL Handshake Failure: If the SSL handshake between Ranger and the services fails, inspect the logs (/var/log/ranger/ for Ranger, and /var/log/hadoop/ for Hadoop services) for SSL-specific errors like "Certificate not trusted" or "Invalid certificate."
Common Issues and Fixes
- The SSL Certificate Expiration: If a certificate has expired, the services reject connections. Use keytool to inspect the expiration date of certificates:
keytool -list -v -keystore /path/to/truststore.jksRenew the expired certificates and re-import them into the truststores if necessary.
- Truststore Password Issues: If the password for the truststore is incorrect in the configuration files (e.g., Ranger Plugin properties), the plugin fails to initialize the SSL context. Ensure the correct password is set and matches the one used during truststore creation.
- Permission Errors: Make sure that the truststore files are accessible by the user running the service (e.g., hdfs for HDFS, hive for Hive):
ls -l /path/to/plugin-truststore.jksModify the permissions, if necessary:
chmod 640 /path/to/plugin-truststore.jkschown hdfs:hadoop /path/to/plugin-truststore.jks- Hostname Mismatch: If the Common Name (CN) in the certificate does not match the hostname of the service, the SSL connections fail. Ensure the certificate is issued to the correct hostname and that the CN matches the FQDN.