Title
Create new category
Edit page index title
Edit category
Edit link
Obfuscating LDAP Bind Password for Zeppelin
Migrate the Zeppelin LDAP bind password from plain-text configuration to the Hadoop Credential Store (JCEKS) to comply with security best practices.
Scope
- Zeppelin integrated with LDAP authentication
- Ambari-managed Zeppelin
- Hadoop Credential Provider (JCEKS)
- Applies to clusters with LDAP-enabled Zeppelin UI
Prerequisites
Ambari LDAP must already be configured and obfuscated
- Refer: ODP-5149 | Obfuscating LDAP password in Ambari
LDAP authentication validated for Ambari
Hadoop CLI available on Zeppelin host
Zeppelin service stopped/restarted as required
Step 1: Configure LDAP for Zeppelin (Baseline Setup)
Update the following configuration in Ambari UI:
Zeppelin → Configs → Advanced zeppelin-shiro-ini
[main]ldapRealm = org.apache.zeppelin.realm.LdapRealmldapRealm.contextFactory.url = ldaps://10.100.11.29:1636ldapRealm.contextFactory.systemUsername = cn=admin,dc=acceldata,dc=celdapRealm.contextFactory.systemPassword = passw0rdldapRealm.userDnTemplate = uid={0},ou=users,dc=acceldata,dc=celdapRealm.contextFactory.environment[ldap.searchBase] = dc=acceldata,dc=celdapRealm.contextFactory.authenticationMechanism = SIMPLEldapRealm.contextFactory.environment[java.naming.security.protocol] = sslldapRealm.contextFactory.environment[java.naming.referral] = followsecurityManager.realms = $ldapRealmsessionManager = org.apache.shiro.web.session.mgt.DefaultWebSessionManagercacheManager = org.apache.shiro.cache.MemoryConstrainedCacheManagersecurityManager.cacheManager = $cacheManagercookie = org.apache.shiro.web.servlet.SimpleCookiecookie.name = JSESSIONIDcookie.httpOnly = truesessionManager.sessionIdCookie = $cookiesecurityManager.sessionManager = $sessionManagersecurityManager.sessionManager.globalSessionTimeout = 86400000shiro.loginUrl = /api/login[urls]/api/version = anon/** = authcRestart Zeppelin and validate LDAP login using an LDAP user.
Zeppelin user dashboard
All LDAP users can log in to Zeppelin UI.
Since you added the password in plain text, you need to obfuscate this using Hadoop credentials.
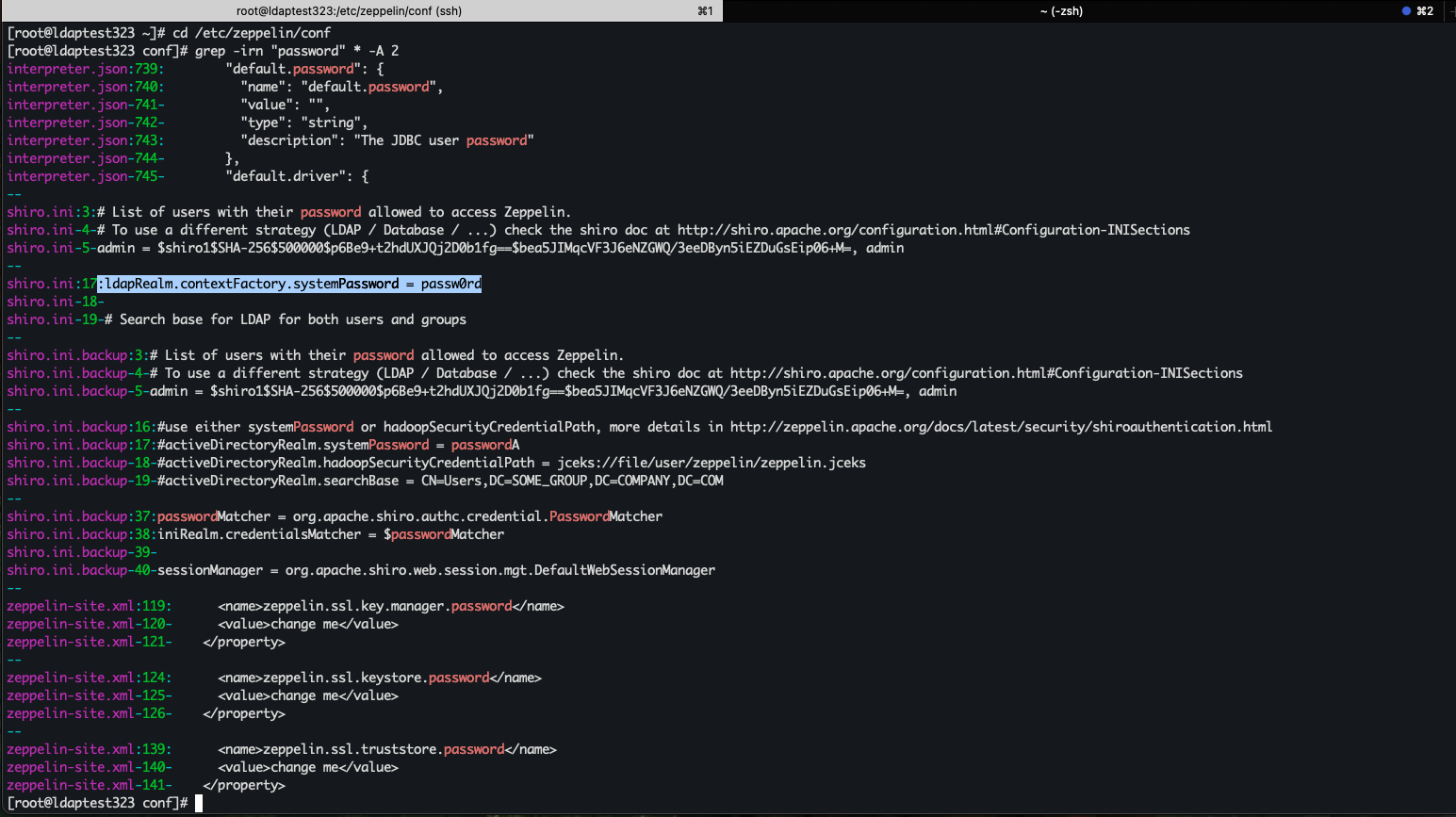
Step 2: Obfuscate Zeppelin LDAP Bind Password
Step 2.1: Move Plain-text Password to JCEKS
Run the following commands on the Zeppelin host:
# Extract LDAP bind password from shiro.iniLDAP_PASSWORD=$(grep "ldapRealm.contextFactory.systemPassword" /etc/zeppelin/conf/shiro.ini | grep -v "^#" | sed 's/.*= *//')# Create credential in JCEKShadoop credential create zeppelin_ldap_pass \ -provider jceks://file/var/lib/zeppelin/zeppelin.jceks \ -value "$LDAP_PASSWORD"# Secure the keystorechown zeppelin:zeppelin /var/lib/zeppelin/zeppelin.jcekschmod 600 /var/lib/zeppelin/zeppelin.jceks# Verify alias creationhadoop credential list -provider jceks://file/var/lib/zeppelin/zeppelin.jceksStep 2.2: Reference JCEKS in Zeppelin Configuration
2.2.1 Set Credential Provider Path
Ambari → Zeppelin → Configs → Advanced zeppelin-env
Add at the end:
export HADOOP_CREDENTIAL_PROVIDER_PATH="jceks://file/var/lib/zeppelin/zeppelin.jceks"2.2.2 Update zeppelin-shiro-ini
Replace the plain-text password with the credential alias:
ldapRealm.contextFactory.systemPassword = #{zeppelin_ldap_pass}Step 3: Restart & Validation
ambari-server restart(or restart Zeppelin service via Ambari UI)
Validation Steps
- Log in to Zeppelin UI using LDAP users
- Ensure no authentication errors in:
/var/log/zeppelin/zeppelin-server.log- Confirm no plain-text password exists in
shiro.ini
The screenshot below is a reference to the users available to Zeppelin.
Outcome
- LDAP bind password removed from plain-text configuration
- Password securely stored in Hadoop Credential Store (JCEKS)
- Zeppelin authentication continues to function as expected
- Compliant with MSTP security hardening standards