This page describes securing Kudu with Kerberos authentication and Ranger.
Security: Kerberos Authentication
If Kerberos is enabled in your cluster, authentication between Kudu masters and tablet servers is automatically enabled. Kudu also issues its own internal certificates to servers in the cluster, so you do not need to manually configure SSL certificates.
Integrate Ranger with Kudu
You can integrate Apache Ranger with Kudu to manage fine-grained access control.
- By default, the
kuduuser is added to thesuperusers_acllist. Users in this list bypass Ranger permissions. This is necessary for Kudu cluster maintenance tasks (see Administer Kudu for details). - To enable Ranger, select Enable Ranger in Ambari.
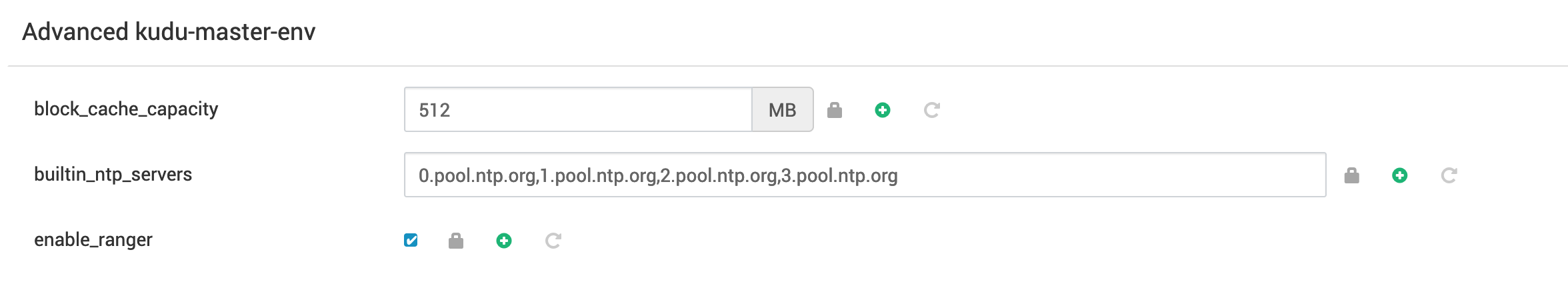
Ranger with SSL
When using Ranger with SSL, you must import the Ranger certificate on each node running a Kudu master or tablet server.
Example:
echo -n | openssl s_client -connect $RANGER_HOST:$RANGER_PORT | sed -nE '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > ranger.pemkeytool -import -alias ranger-cert -file ranger.pem -keystore /etc/pki/java/cacerts -storepass $your_storepassIn addition:
- Set the keystore and truststore passwords in the Ambari UI.
- Configure the following properties as needed
keystore.credential.filetruststore.credential.file
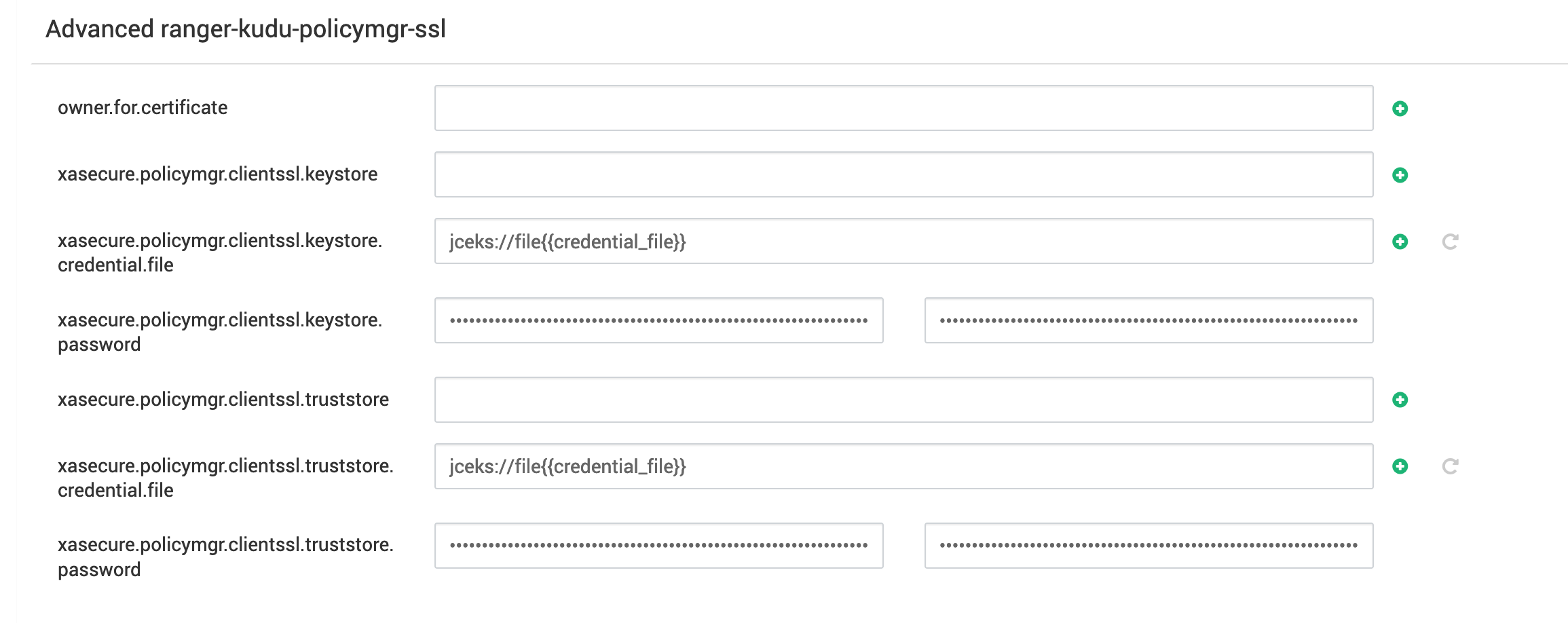
Best Practices with Ranger
- Keep the
impalauser as a superuser. - Apply Ranger policies to Impala instead of Kudu for any tables that should be accessible through Impala.
You can refer to the example below for creating a Ranger policy.
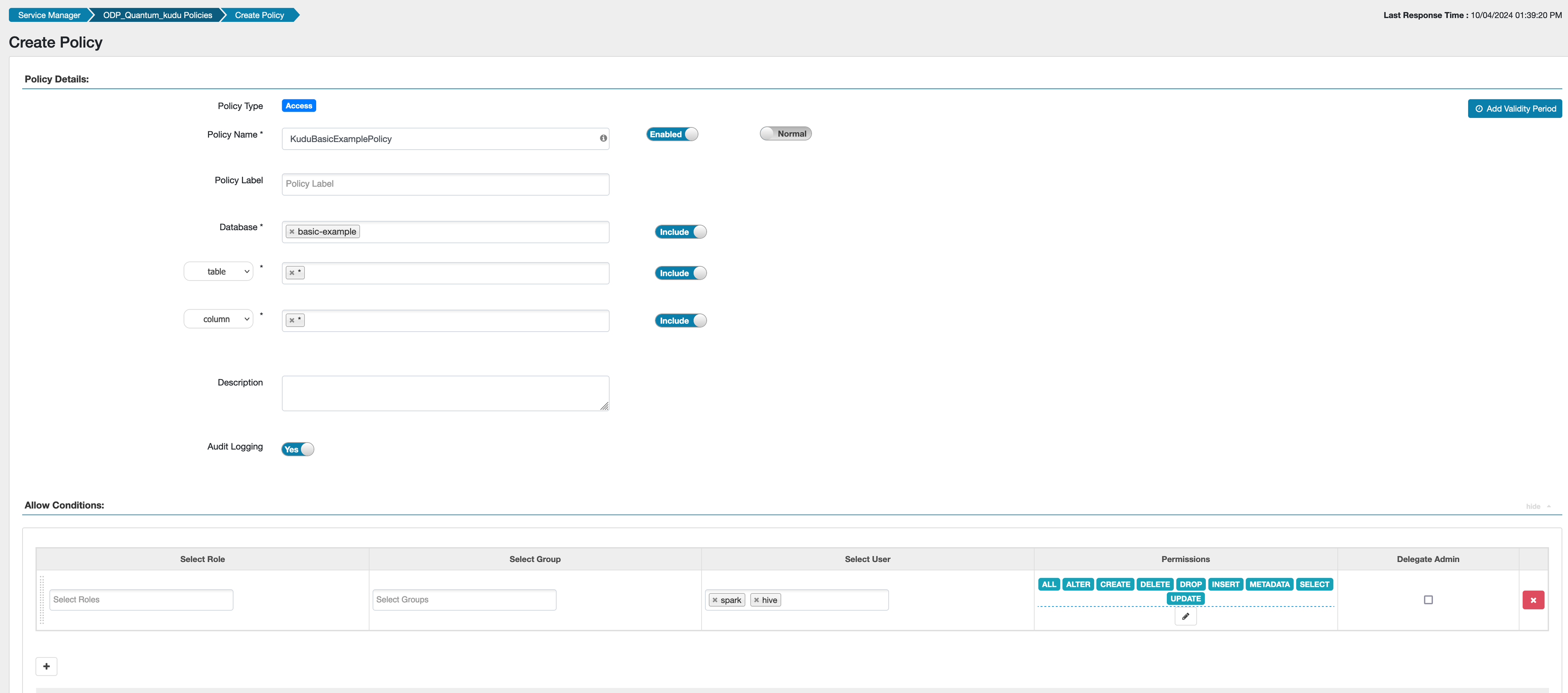
Example Ranger Policy
You can define Ranger policies using the {OWNER} placeholder. This allows privileges to be automatically granted to table owners.
For example:
- Create a policy with the
{OWNER}username for a resourcedb= → table=. - This policy applies automatically when the table owner accesses their table.
This approach eliminates the need to create individual policies for each table while avoiding overly broad access grants.
For more information about securing a Kudu cluster, see Apache Kudu Security.