Title
Create new category
Edit page index title
Edit category
Edit link
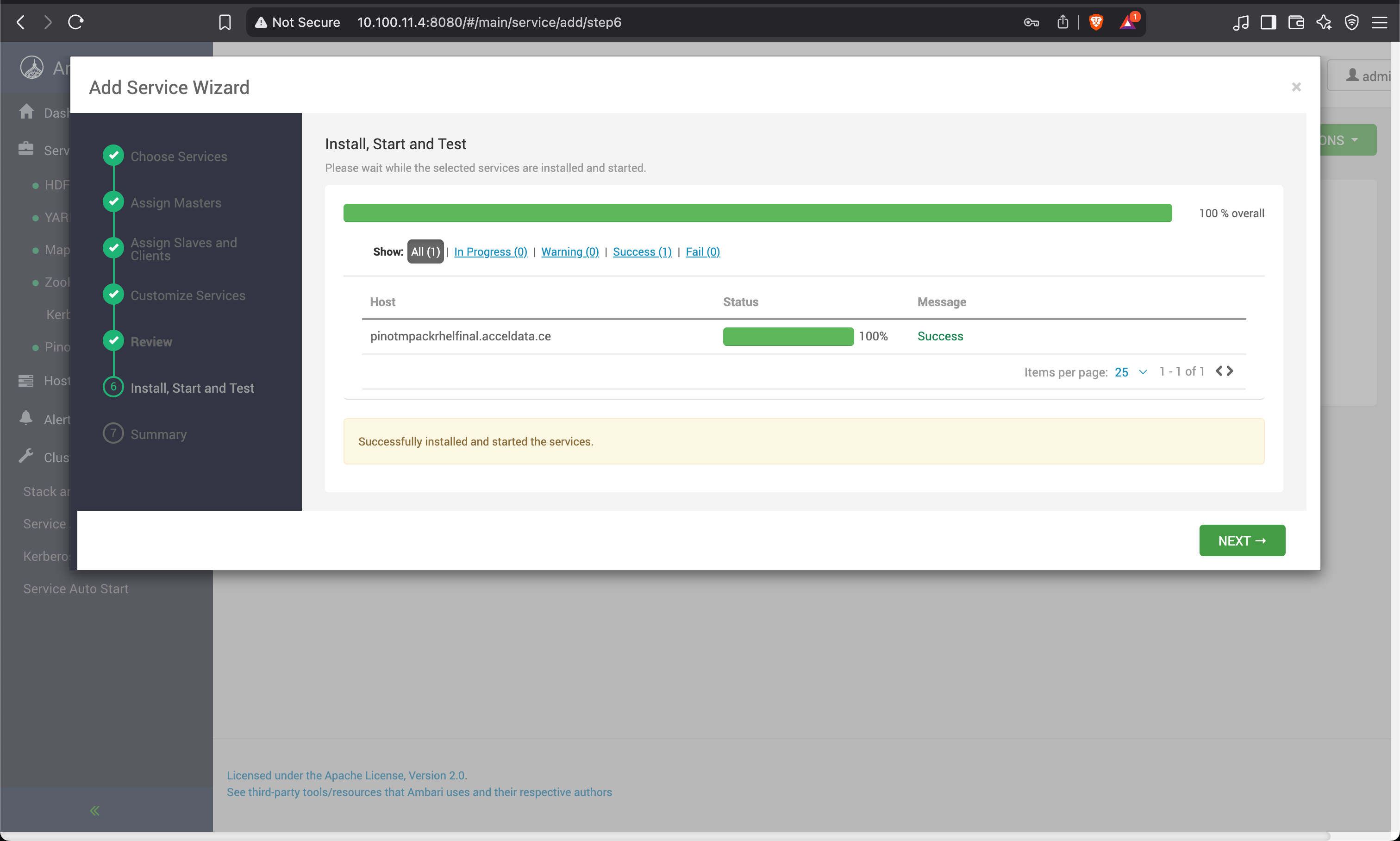
Install Knox
Install Knox
Perform the following steps to install Knox.
Knox Master Secret - Acceldata@01
Add entry for the Pinot service in the topology.
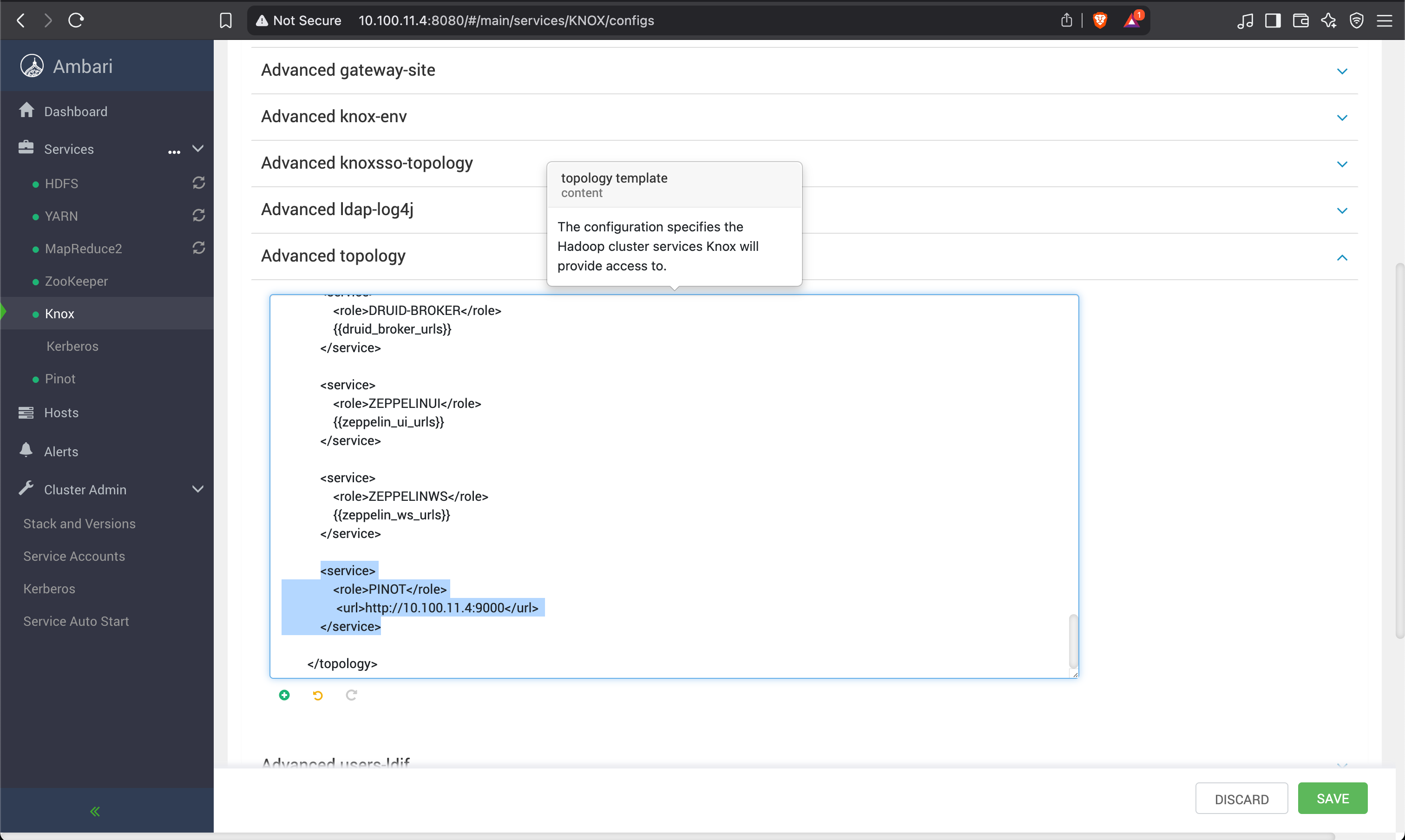
To configure Knox for Pinot in the current release [3.2.3.X], follow the steps outlined below.
- Create service directory for Pinot under Knox installation path.
mkdir -p /usr/odp/3.2.3.3-2/knox/data/services/pinot/1.3.0/chown -R knox:knox /usr/odp/3.2.3.3-2/knox/data/services/pinot- Create and update the content of below files.
/usr/odp/3.2.3.3-2/knox/data/services/pinot/1.3.0/rewrite.xmlPaste the content of the rewrite file present on this link.
/usr/odp/3.2.3.3-2/knox/data/services/pinot/1.3.0/service.xmlPaste the content of the service file present on this link.
- Save and restart Knox.
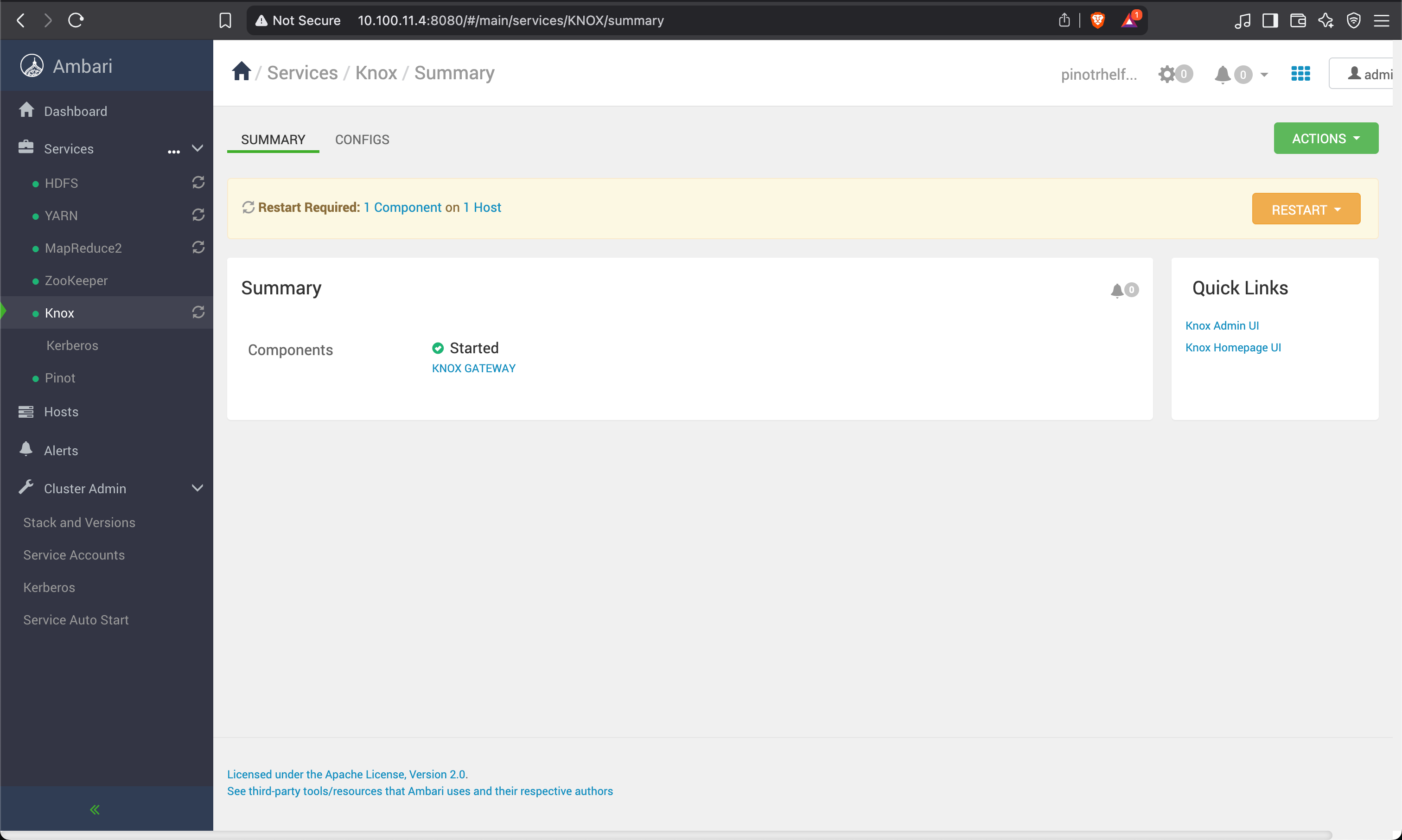
Start the demo LDAP Server
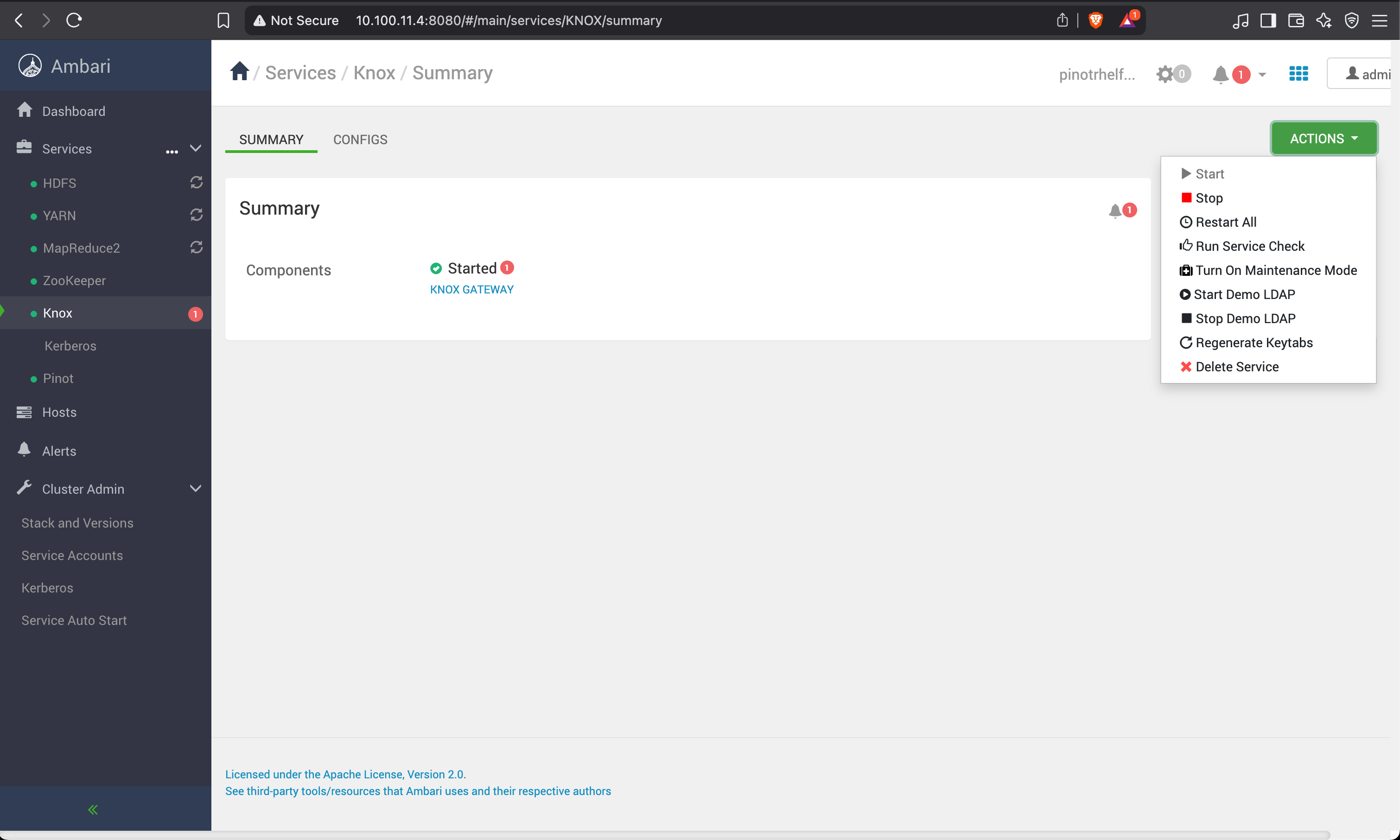
If you are enabling Knox, disable the basic auth option.
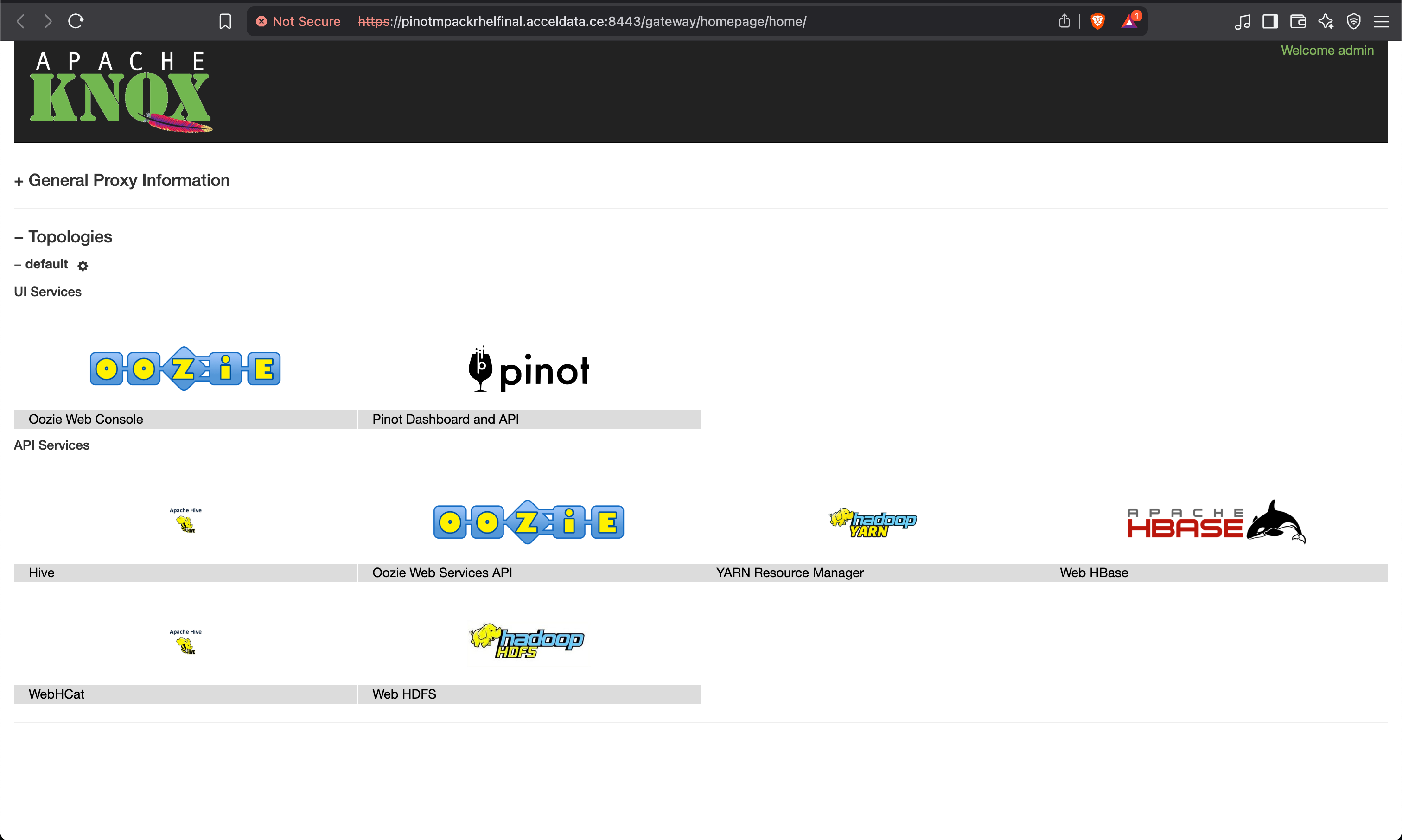
Knox Homepage UI
Access the Knox Homepage UI, click the Pinot service, and enter username and password.
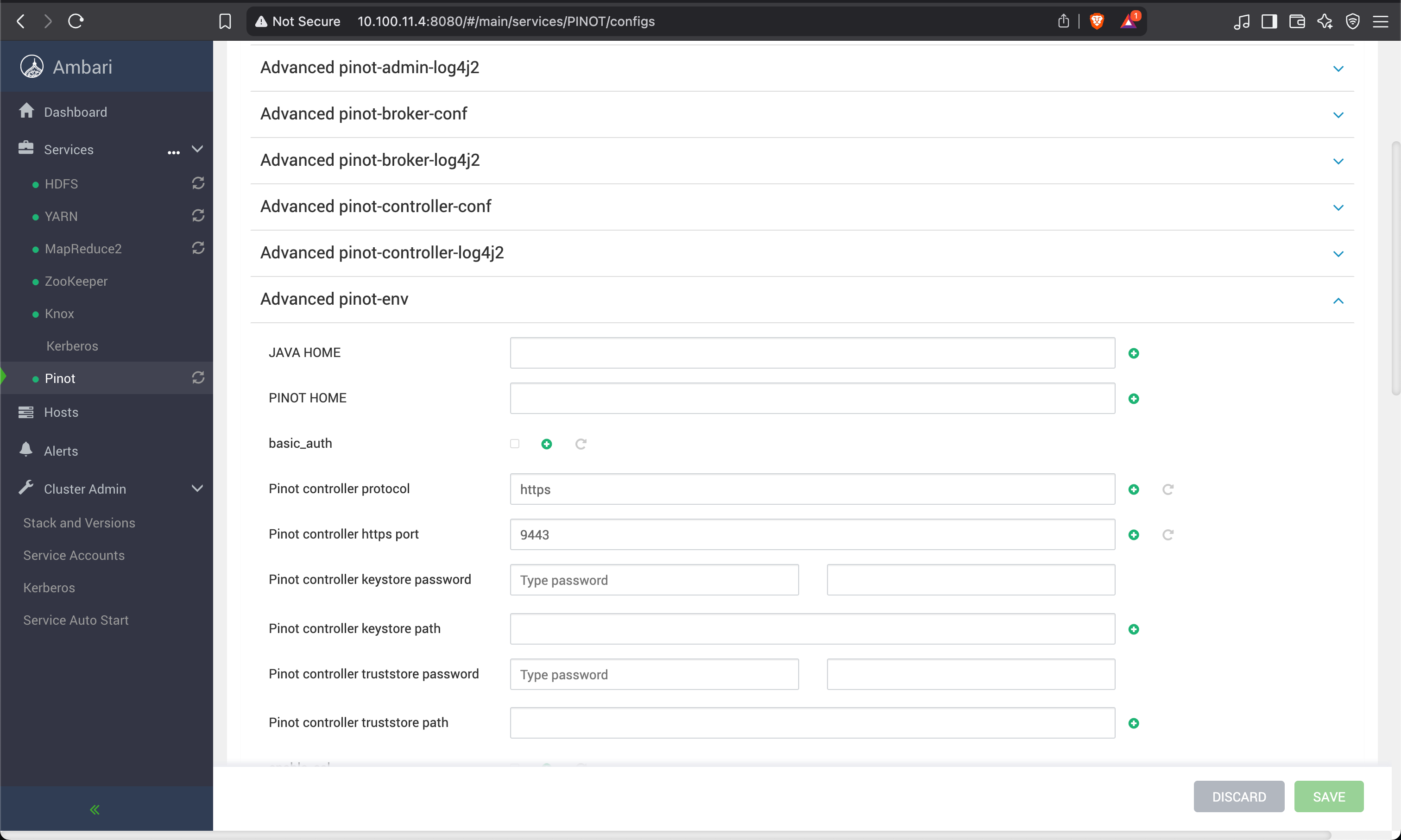
SSL Enablement on the Controller UI
To generate the pinot-keystore.p12 and pinot-truststore.p12 files for securing the Pinot Controller UI using SSL/TLS, follow these steps:
Prerequisites
- Java installed (
keytoolcomes with JDK) - OpenSSL (optional for importing existing certs)
- Directory
/etc/pinot/ssl/exists and has proper permissions
Generate Keystore and Truststore for Pinot Controller
- Generate a Keystore (Self-Signed Certificate)
sudo mkdir -p /etc/pinot/sslkeytool -genkeypair \ -alias pinot-controller \ -keyalg RSA \ -keysize 2048 \ -validity 365 \ -keystore /etc/pinot/ssl/pinot-keystore.p12 \ -storetype PKCS12 \ -storepass changeit \ -keypass changeit \ -dname "CN=pinot-controller, OU=Data Platform, O=YourOrg, L=YourCity, ST=YourState, C=US"storepassandkeypasscan be the same.- Replace
CNand other DNAME values as needed.
- Create the Truststore
If you're using self-signed certs, export the public certificate from the keystore and import it into the truststore.
Export certificate from keystore:
keytool -exportcert \ -alias pinot-controller \ -keystore /etc/pinot/ssl/pinot-keystore.p12 \ -storetype PKCS12 \ -storepass changeit \ -file /etc/pinot/ssl/pinot-controller.crtImport into a new truststore
keytool -importcert \ -alias pinot-controller \ -file /etc/pinot/ssl/pinot-controller.crt \ -keystore /etc/pinot/ssl/pinot-truststore.p12 \ -storetype PKCS12 \ -storepass changeit \ -noprompt- Secure Permissions (Optional, but Recommended).
sudo chmod 640 /etc/pinot/ssl/*.p12sudo chown pinot:pinot /etc/pinot/ssl/*.p12- Configure Pinot to use the SSL Certificate.
Edit controller.conf or wherever your Pinot Controller properties are set:
controller.https.port=8443controller.ssl.keyStore.path=/etc/pinot/ssl/pinot-keystore.p12controller.ssl.keyStore.password=changeitcontroller.ssl.trustStore.path=/etc/pinot/ssl/pinot-truststore.p12controller.ssl.trustStore.password=changeitcontroller.ssl.protocol=TLScontroller.ssl.enabled=trueRestart the Pinot Controller after updating the configuration.
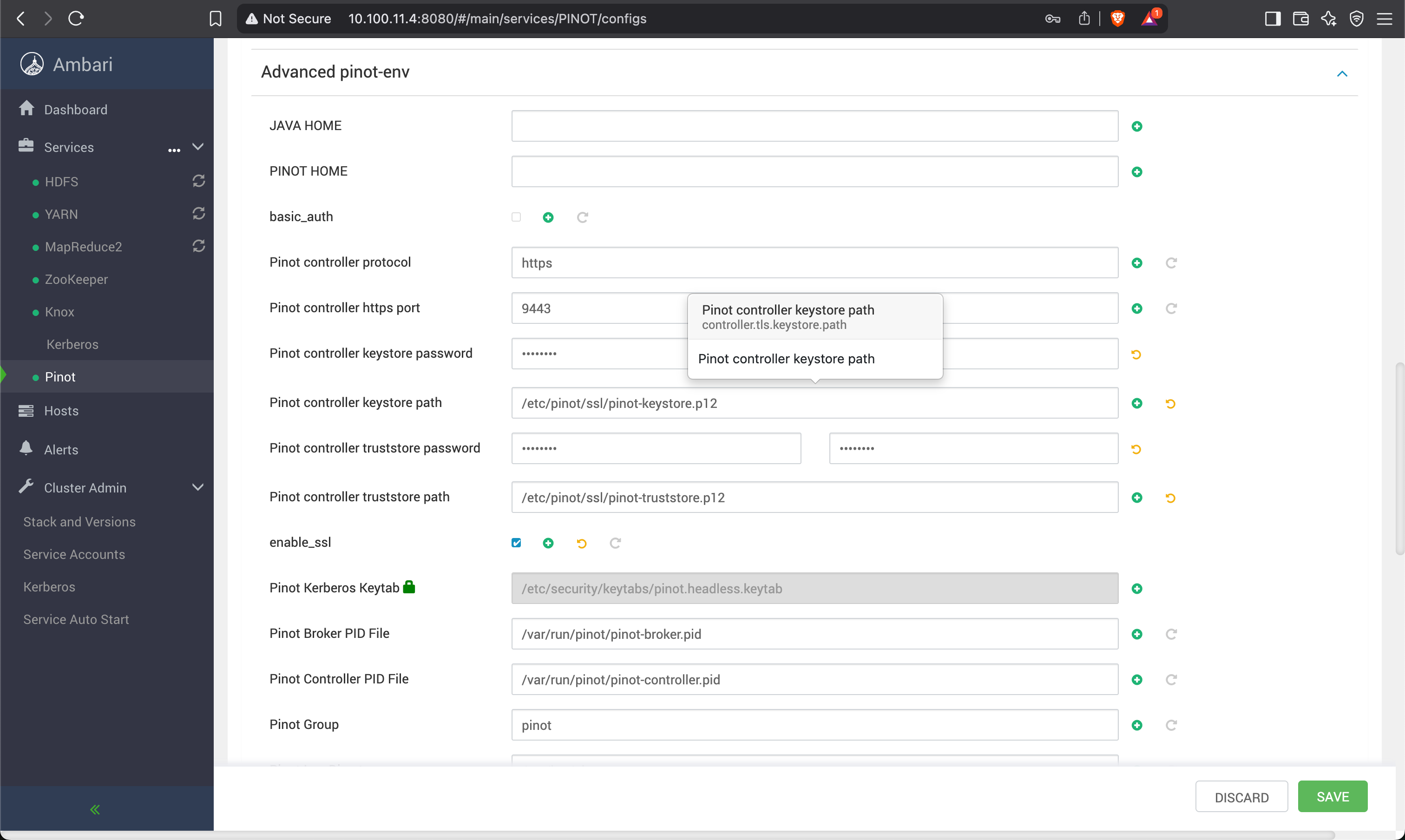
Save and restart the service.